
As a business that handles customer data, your business must understand what personally identifiable information (PII) and sensitive personal information (SPI) are and how to protect them.
You’ve come to the right place to find out what both of these terms mean and how they’re different. This article will cover PII vs SPI in detail, along with instructions to safeguard both PII and SPI.
Let’s dive right in.
Key Takeaways
PII is any information that can (on its own or together with other relevant data) identify a person’s identity.
SPI is a type of PII that, if revealed, can harm a person.
SPI includes SSNs, financial information, medical records, criminal records, and more.
PII Explained

PII or personally identifiable information is any information that, when used on its own or in combination with other relevant data, identifies a person.
PII can be sensitive and non-sensitive.
Sensitive PII, such as a person’s social security number, tax identification number, financial account records, driver’s license, biometric data, etc., can be used on its own to identify a person, as it naturally belongs to only one individual.
Non-sensitive PII, in comparison, such as a name, person’s date or place of birth, gender, race, business address, email address, or geographical location, cannot identify a person on its own, so it must be used in combination with other non-sensitive PII.
SPI Explained

SPI, or sensitive personal information, is similar to PII in that it also can be used to identify a person.
Different data protection regulation defines SPI differently. Let’s cover how the GDPR and CPRA define SPI:
GDPR on SPI
The EU’s General Data Protection Regulation (GDPR) does not use the term “sensitive personal information” but instead “special categories of personal data.”
Under Article 9(1) of GDPR:
“Processing of personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, and the processing of genetic data, biometric data to uniquely identify a natural person, data concerning health or data concerning a natural person’s sex life or sexual orientation shall be prohibited.”
From this, we can see that the GDPR considered the following personal data to be “sensitive”:
Genetic and biometric data that are processed for the sole purpose of identifying a person
Personal data revealing a person’s ethnic or racial origin
Personal data about a person’s beliefs (political, religious or philosophical
Data that concern someone’s sexual life or sexual orientation
Health information
Trade-union memberships
CPRA on SPI
The California Privacy Rights Act (CPRA), unlike GDPR, uses the term “sensitive personal information.”
In Section 1798.140(o)(1), CPRA defines SPI as:
“Personal information that reveals a consumer’s social security, driver’s license, state identification card, passport number, account login, financial account, debit card, or credit card number in combination with any required security or access code, password, or credentials allowing access to an account, precise geolocation, racial or ethnic origins, religious or philosophical beliefs, or union membership, contents of a consumer’s mail, email, and text messages unless the business is the intended recipient of the communication and genetic data.”
The Chinese PIPL also defines SPI in Article 28, and so do many other regulations, so be sure to check your applicable regulations for what is specifically covered.
Nick Henderson-Mayo, director of learning at Vinciworks, says:
“Different types of data, such as special category data under GDPR and Sensitive Personal Information under US laws, will often overlap. Therefore, similar data protection methods can be used to protect and secure this information.
Generally, it is useful to consider the strongest data protection requirements a company has to follow (usually GDPR) and protect all personal data in this manner. With so many overlapping laws and regulations, the impact of a breach can lead to significant fines and regulatory action.”
Not sure how to get your data protection efforts to meet the requirements of GDPR? Get in touch with us today for a free consultation.
Key Differences Between PII vs SPI
Why some PII data is considered “sensitive” and others not is because certain PII can, if they get into the wrong hands, be used against the person and be potentially harmful or dangerous to them.
For example, some information that could cause great harm in the wrong hands includes Social Security Numbers (SSN), medical history, and financial account information, among others.
On the other hand, PII that a person would normally reveal publicly, like their name, email address, or phone number, is generally not considered as “sensitive,” but only PII.
Additionally, as the name implies, sensitive information is more “sensitive” than typical PII, which means that regulations surrounding SPI are often more stringent since there’s more harm if the data gets leaked. SPI will also often bear a higher consequence for data breaches.
Of course, that still doesn’t mean that, as a data controller, your business should not do everything in its power to protect this customer data as well.
Similarities Between PII vs SPI
Personally identifiable information and sensitive information both relate to a specific individual and can be used to identify or be linked to him or her.
Both PII and SPI also have regulations and laws in place to protect them, such as the General Data Protection Regulation (GDPR) in Europe and the Health Insurance Portability Accountability Act (HIPAA) in the United States. These regulations aim to prevent unauthorized access, use, or disclosure of PII/SPI.
Both also raise significant data security and privacy concerns and must be handled and protected with utmost care to protect the data subject’s privacy rights and avoid identity theft, data breach, or other privacy violations.
Furthermore, both PII and SPI require obtaining informed and explicit consent from the person to whom they belong if your organization wants to process their data.
Steps to Secure PII & SPI
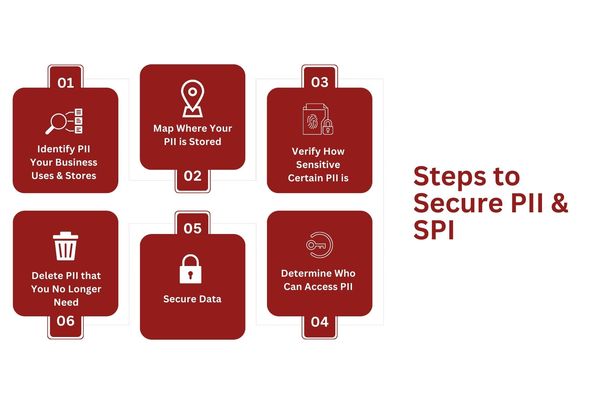
If they get into the wrong hands, PII and SPI can be used to harm the individual.
This is why data protection regulation puts special emphasis on securing these two categories of personal data.
As a data controller, your company also must take certain steps to secure your consumers’ PII and SPI against compromise and/or loss. Here are specific steps you can take to mitigate compliance and security risks:
Identify what PII Your Business Uses and Stores
First, identify the types of PII that your business uses and stores. Depending on the nature of your business, this might be names, financial information, medical records, emails, phone numbers, etc. Create an inventory of all the PII in your possession.
Map Where Your PII is Stored
The next step in protecting your customers’ PII is to know exactly where you are storing it.
You might be storing PII and SPI in file cabinets, servers, on the cloud, employee laptops, USB sticks, and other places.
Once you have a complete list of where all the data is stored, assess each storage location’s security measures to see if it meets compliance and best-practice standards.
Verify How Sensitive Certain PII is
We are now getting to the sensitive personal information.
As we explain throughout this article, SPI is a subset of PII. In other words, all SPI are PII, but not all PII are SPI.
Can a single piece of data uniquely identify a person and potentially cause harm if leaked? You should consider this data as highly sensitive.
This could include social security numbers, credit card information, or personal health records.
Determine Who Can Access PII
The fewer people have access to PII, especially SPI, the lower the chance of it making its way into the wrong hands or of loss and data breach.
Limit the access to your customer’s PII to only those people and departments that are necessary to process it. This is easier said than done, and it might require changing the way your organization operates.
Minimize, Anonymize, Pseudonimize, and Encrypt
Data minimization is one of the seven principles of GDPR and is often among the main principles of other data regulations. This principle states that personal data must be adequate, relevant, and limited to what is necessary concerning the purposes for which it is processed.
However, even if you use only the minimum data necessary, it can be enough to identify a person or be potentially harmful to their privacy.
This is why we also recommend that you anonymize or pseudonymize and encrypt this data whenever possible.
Anonymization means that data is “scrubbed” of any information that can be a direct or indirect identifier of the identity of the person.
For instance, if we have the following original data:
Name: Jim Jones
Email: jimjones@email.com
SSN: 123-456-789-0
Then anonymized data would look something like this:
Name: #547
Email: #547’s email
SSN: #547’s SSN
The point here is that nothing links anonymized to the original data, so anonymized data cannot identify a person.
Pseudonymized data is similar to anonymized, but some information must be retained. This can be to achieve compliance or if the company still needs the data for a specific purpose.
A typical example of pseudonymized data would be if a company replaced the original data (say, a person’s full name) with a unique identifier. On its own, this identifier does not reveal that person’s identity but, if combined with other identifiers, can link back to them.
Finally, we have encryption. Encryption ensures data confidentiality and security by making the data unreadable to anyone but someone with the right decryption key.
Typically, when sensitive personal data is involved, businesses use a data protection officer to
Delete PII that You No Longer Need
Finally, whether the PII and SPI are anonymized, pseudonymized, or encrypted, you should only retain data for as long as the specific purpose for which you are processing data requires it.
When you no longer need the data, you should delete it. This might be tricky from a record-keeping perspective. However, it is essential that you build efficient processes around data deletion.
Need help securing PII and SPI? Get in touch with us today for a complimentary consultation.
PII vs. SPI in the Age of AI
The distinction between PII (Personally Identifiable Information) and SPI (Sensitive Personal Information) becomes even more critical in the age of AI. AI’s ability to analyze and infer data means that what was once just “identifiable” is now often treated as “sensitive” due to the potential for harm if misused.
1. PII (Personally Identifiable Information)
As previously discussed, PII is information that can be used to identify, locate, or contact an individual. In the AI context, this definition is expanded by the system’s ability to link disparate data points.
-
Core Examples: Full Name, Date of Birth, Physical Address, Email Address, Account Numbers.
-
AI Context: An AI system uses PII for identity resolution (linking all data records back to a single person) and personalization (targeting ads or content). The risk is primarily one of identity theft or unauthorized communication.
2. SPI (Sensitive Personal Information)
SPI is a specific sub-set of PII that, if compromised, could lead to severe, unique, and discriminatory harm to an individual. It carries a higher regulatory compliance burden and usually requires explicit, affirmative consent for processing.
-
Core Examples:
-
Health and Medical Information: Diagnostics, treatment records, genetic data.
-
Financial Data: Credit card numbers, bank account details.
-
Protected Characteristics: Racial or ethnic origin, political opinions, religious beliefs, sexual orientation.
-
Biometric Data: Facial recognition templates, fingerprints (when used for identification).
-
Trade Union Membership.
-
3. The SPI Risk Amplified by AI (The “Inference Problem”)
AI systems elevate the risk associated with SPI in two primary ways:
A. Inferential SPI Creation
AI models can take non-sensitive PII (like your browsing history or purchase data) and use it to infer a highly sensitive trait, effectively creating SPI.
-
Example: An AI model analyzes an individual’s subscription history to certain magazines, donation patterns, and frequented web forums. It then infers their political opinions or religious beliefs. Under laws like the CPRA, these inferences are often treated as sensitive personal information that the individual has the right to limit the use of.
B. Harm Magnification
When AI-created SPI is compromised or misused, the potential harm is significant:
-
Discrimination: Inferred SPI regarding race, health, or political beliefs can be used to unfairly deny an individual access to loans, housing, or employment.
-
Social Engineering: Highly detailed SPI (like specific health conditions or financial struggles) can be used to craft sophisticated phishing or social engineering attacks that are far more effective than those using simple PII.
While PII is the key to the individual, SPI relates to their most protected characteristics. AI blurs the line by turning PII into inferred SPI, demanding that organizations apply the highest level of protection to any data that could potentially lead to discriminatory outcomes.
FAQs
What is SPI and PII?
SPI, or sensitive personal information, is any information that can identify a person but also be in some way harmful to them if it gets into the wrong hands.
PII, or personally identifiable information, is wider (SPI is a subcategory of PII) in that it refers to any personal information that can, solely or with other data, identify a person, though it often doesn’t have to be harmful if it does.
Learn what PII is used for in this article.
Is biometric data SPI or PII?
Since SPI is a subcategory of PII, biometric data is both. Specifically, biometric data that is processed to identify a person and can be harmful is considered “sensitive.”
Learn more about compliance on our education page here.
Are PI and SPI the same?
PI or personal information is a wider category, and not all are sensitive.
For example, publicly available PI is not generally considered sensitive. This can include a person’s email address, birth date, employment or education history and information, general demographic data, etc., which are usually not sensitive.
Want to compare PII vs PI? Click here to learn more.
What is SPI in data privacy?
Sensitive personal information (SPI) refers to information that can be used to identify an individual and also be potentially harmful to the individual in case of a data breach or compromise.
Learn everything you need to know about data privacy compliance services here.
Which is not a PII?
Personal information (PI) is a broader term than personally identifiable information (PII).
PI refers to any information that relates to an individual but can’t be used to identify them. In comparison, PII is any information that can be used to identify the individual.
For example, the name John is PI, but not PII because there are over 5 million Johns out there. However, if we add a second name to this, it’s now much more likely to identify this individual.
Want help securing PII and SPI? Get in touch with us today.
How Can Captain Compliance Help?
Ultimately, protecting personal data is the focus of every data privacy law, and it should also be in the data privacy and security efforts of your business.
If you need help safeguarding PII and/or SPI properly, Captain Compliance can help you with this process and take this burden off your shoulders so you can focus on business. Get in touch with us today to find out how you can safeguard your personal data.