Cybersecurity and privacy compliance are no longer parallel tracks they’re converging requirements that demand integrated strategies. Organizations that treat security and privacy as separate domains inevitably face gaps that lead to regulatory violations, data breaches, and substantial financial penalties that we can help remediate and protect against. The reactive approach of addressing compliance after security implementations results in expensive retrofits, audit failures, and regulatory scrutiny all of which can be avoided if you’re proactive.
The proactive alternative embedding privacy requirements into cybersecurity architecture from inception not only prevents costly fines but transforms compliance from a liability into a competitive advantage just as Apple has used privacy and security as a competitive edge to become one of the largest enterprises in the world. This approach, central to effective privacy management, requires understanding that modern privacy regulations (GDPR, CCPA, HIPAA, CIPA, ECPA, CPRA, state privacy laws, and international frameworks) don’t prescribe specific security tools. Instead, they mandate outcomes: demonstrable, proportionate protection of personal data with auditable evidence of technical safeguards.
This comprehensive guide provides six technical pillars for building cybersecurity programs that satisfy complex privacy regulations while establishing resilient security postures.
If you’d like help with your data governance and privacy posture book a demo with our software team to learn how we can integrate the software tools from Captain Compliance to help automate your requirements.
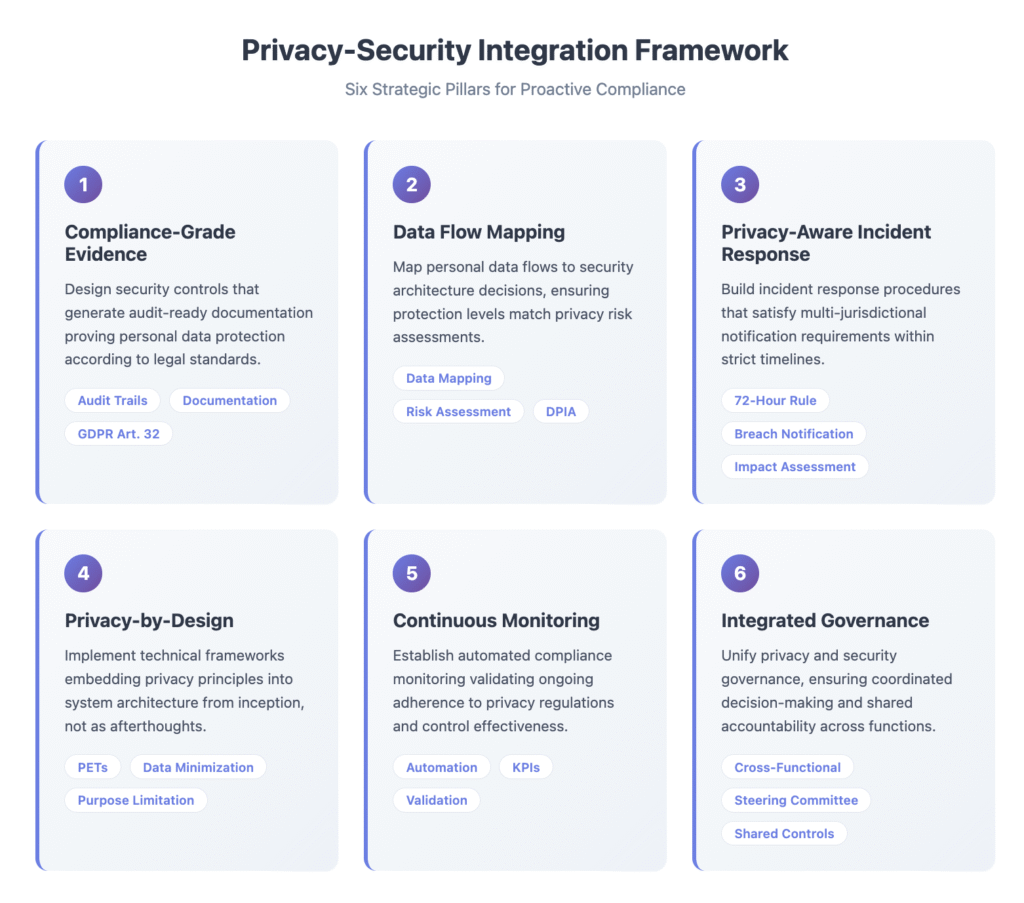
1. Design Security Controls That Generate Compliance-Grade Evidence
Privacy regulations fundamentally changed what cybersecurity programs must prove. Traditional security focuses on preventing unauthorized access and maintaining system integrity. Privacy compliance demands documentation proving that specific technical measures protect personal data according to legal standards, not merely technical best practices.
Understanding Legal Technical Standards
GDPR Article 32 requires “appropriate technical and organizational measures” including encryption that renders data “unintelligible to any person who is not authorized to access it.” This legal language translates to specific technical requirements:
Encryption Implementation: AES-256 or equivalent with documented key management procedures, key rotation schedules, and access control lists showing who possesses decryption capabilities
Access Logging: Comprehensive audit trails capturing not just WHO accessed systems, but WHAT personal data categories were accessed, WHEN access occurred, and WHY access was legally justified under processing purposes
Pseudonymization Evidence: Technical documentation proving personal data is separated from direct identifiers, with separate security controls protecting the linkage mechanism
CCPA has new rules coming out each year some in 2026 and some relating to Governor Newsome’s new CCPA 2027 audit requirements that evaluate whether security controls specifically protect personal information as defined under California law—which includes identifiers, commercial information, biometric data, internet activity, geolocation data, professional information, and inferences drawn from this data. Security controls must demonstrate protection across all these categories with differentiated measures based on sensitivity.
HIPAA’s Security Rule requires covered entities to implement “technical safeguards” (164.312) including access controls, audit controls, integrity controls, and transmission security. However, HIPAA’s enforcement history shows that technical implementation without documented risk analysis, security management processes, and workforce training results in violations—even when encryption is properly deployed.
Implementing Evidence-Generating Security Architecture
Tool Selection Framework:
When evaluating security platforms, apply this compliance-oriented assessment:
- Audit Trail Granularity: Can the tool capture personal data access at the record level, not just system level? Does it log the legal basis or processing purpose for each access event?
- Retention and Retrieval: Can audit logs be retained for regulatory-mandated periods (typically 3-7 years depending on jurisdiction) and retrieved within 72-hour breach notification windows?
- Data Classification Integration: Does the tool recognize personal data categories (PII, SPI, PHI, financial data) and apply differentiated controls automatically?
- Regulatory Reporting: Can the platform generate reports mapping to specific regulatory frameworks (GDPR Article 32 technical measures, CCPA reasonable security requirements, HIPAA technical safeguard standards)?
Example Implementation:
A SIEM (Security Information and Event Management) platform configured for privacy compliance doesn’t just aggregate security events—it correlates events with data classification tags, processing purposes from privacy documentation, and legal basis records. When an employee accesses customer health records, the compliant SIEM logs:
- Identity and role of accessor
- Specific data categories accessed (PHI under HIPAA definitions)
- Timestamp and access duration
- Processing purpose (treatment, payment, healthcare operations)
- Legal basis (consent, legal obligation, legitimate interest)
- Result (successful access, denied access, partial access with redaction)
This granular logging provides both security monitoring AND compliance evidence that access controls protect personal data according to regulatory requirements.
Bridging the Evidence Gap
Many organizations deploy technically sound security controls that fail privacy audits because they lack compliance-focused evidence. Address this gap by:
- Creating compliance mappings that document how each security control satisfies specific regulatory requirements across applicable frameworks
- Implementing automated compliance reporting that translates security metrics into regulatory language
- Conducting parallel testing: security penetration testing alongside privacy audit simulations
- Establishing evidence repositories where technical documentation, configurations, logs, and assessments are maintained in audit-ready formats
2. Map Personal Data Flows to Security Architecture Decisions
Traditional security architecture prioritizes network topology, system criticality, and threat vectors. Privacy-compliant security architecture adds a critical dimension: personal data flows and their associated legal obligations.
Conducting Privacy-Driven Data Mapping
Comprehensive data mapping identifies:
- Data categories: Contact information, financial records, health data, biometric data, location data, behavioral data, children’s data, employee records, sensitive personal data under GDPR Article 9
- Data sources: Where personal data originates (customer input, third-party data brokers, device sensors, public records, inferred data from analytics)
- Processing activities: Collection, storage, analysis, sharing, deletion, and the legal basis for each activity
- Data destinations: Internal systems, third-party processors, cross-border transfers, public disclosure
- Retention periods: How long data is maintained and the legal or business justification
- Subject rights touchpoints: Where individuals exercise access, deletion, correction, portability, and objection rights
This mapping directly informs security architecture by identifying which data flows require enhanced protection under privacy regulations.
Translating Privacy Risk Assessments into Security Requirements
GDPR’s Data Protection Impact Assessment (DPIA), CCPA’s risk assessment requirements, and HIPAA’s Security Risk Assessment serve similar functions: identifying high-risk data processing that triggers enhanced security obligations.
Privacy-Security Integration Framework:
High Risk (triggers: Large-scale profiling, automated decision-making, special category data, children’s data, innovative technologies)
- Required Security: Multi-factor authentication, end-to-end encryption, algorithmic auditing, enhanced monitoring, data minimization controls, privacy-preserving techniques
Significant Risk (triggers: Cross-border transfers, third-party processing, employee monitoring, health/financial data)
- Required Security: Encryption in transit and at rest, processor security assessments, transfer impact assessments, access segmentation
Elevated Risk (triggers: Marketing analytics, behavioral tracking, combined datasets)
- Required Security: Pseudonymization, access logging, consent management integration, purpose limitation controls
Standard Risk (triggers: Basic contact information, transactional data)
- Required Security: Standard encryption, access controls, backup security, incident response procedures
Implementing Data-Specific Security Controls
Create technical implementations that align security measures with data categories:
Example: AI-Driven Customer Analytics Platform
- Data Category: Behavioral data, purchase history, demographic information, inferred preferences
- Privacy Risk: Automated profiling under GDPR Article 22, potential discriminatory outcomes, significant decisions affecting individuals
- Required Security Controls:
- Role-based access control limiting data scientists to aggregated/anonymized datasets
- Production environment with individual-level data accessible only to authorized personnel with documented legitimate purposes
- Algorithm audit trails logging decision factors, confidence scores, and human review touchpoints
- Data minimization controls automatically purging detailed behavioral data after algorithmic training
- Explainability logging enabling responses to subject access requests about automated decisions
- Differential privacy techniques protecting individual data points in analytical outputs
This approach ensures security controls don’t merely protect data from external threats they enforce privacy principles (purpose limitation, data minimization, transparency) through technical measures.
3. Build Incident Response That Satisfies Multi-Jurisdictional Notification Requirements
Cybersecurity incident response traditionally prioritizes containment, eradication, and recovery. Privacy regulations add complex notification obligations with varying timelines, thresholds, and content requirements across jurisdictions.

Understanding Regulatory Notification Complexity
GDPR (Article 33-34): 72-hour notification to supervisory authority; individual notification when high risk to rights and freedoms; must include nature of breach, categories and approximate number of individuals affected, likely consequences, mitigation measures
CCPA/CPRA: No specific breach notification timeline (follows California Civil Code §1798.82); requires notification to California Attorney General if affecting 500+ California residents; consumers must be notified of unauthorized access to unencrypted personal information
HIPAA Breach Notification Rule: Notification to affected individuals without unreasonable delay and within 60 days; HHS notification depends on breach size (500+ individuals requires immediate notification); media notification for breaches affecting 500+ residents in one state or jurisdiction
State Privacy Laws: Virginia CDPA, Colorado CPA, Connecticut CTDPA, Utah UCPA, and others impose varying notification requirements, typically focusing on “personal data” breaches with reasonable security failure thresholds. If you want help with these state privacy frameworks Captain Compliance is your solution to automate privacy compliance requirements
International Regulations: Australia’s Privacy Act (30-day notification), PIPEDA in Canada (as soon as feasible), LGPD in Brazil (reasonable timeframe), and evolving Asian-Pacific frameworks each impose distinct requirements
Designing Privacy-Aware Incident Response Procedures
Phase 1: Detection and Initial Assessment
Within the first hour of incident detection:
- Trigger privacy assessment protocol: Activate parallel privacy analysis alongside technical forensics
- Identify data repositories involved: Cross-reference affected systems with data mapping documentation to determine personal data categories at risk
- Establish notification timeline: Calculate strictest applicable deadline based on jurisdictions involved
- Initiate evidence preservation: Secure logs, access records, and technical findings required for regulatory notifications
Phase 2: Scope and Impact Determination
Within 24 hours:
- Personal data category analysis: Determine exactly which data categories were accessed, exfiltrated, encrypted, or potentially compromised (contact info, financial data, health records, credentials, biometric data, etc.)
- Individual count estimation: Calculate number of individuals affected with geographic breakdown for jurisdictional notification requirements
- Legal consequence assessment: Evaluate risks to individuals (identity theft, financial fraud, discrimination, physical harm, reputational damage) considering data sensitivity and potential misuse scenarios
- Third-party notification evaluation: Identify processors, controllers, or business partners requiring notification under contractual or regulatory obligations
Phase 3: Regulatory Notification Execution
Within 72 hours (GDPR standard; adjust for stricter jurisdictions):
- Supervisory authority notification: Submit required documentation including breach nature, data categories affected, individual counts, consequence assessment, and mitigation measures
- Individual notification preparation: Develop clear, non-technical communication explaining what happened, what data was involved, what individuals should do, and what organization is doing
- Attorney General/regulatory notification: For jurisdictions requiring AG notification, prepare prescribed formats with required information elements
- Processor/partner notification: Inform business partners of breach affecting shared personal data or requiring their notification actions
Phase 4: Remediation and Documentation
- Technical remediation: Implement security improvements addressing root cause of breach
- Compliance documentation: Maintain comprehensive records of incident response, privacy impact assessments, notification decisions, and remediation steps for regulatory inquiries or audits
- Lessons learned integration: Update incident response procedures, data mapping documentation, and security controls based on incident findings
Pre-Incident Preparation Requirements
Effective incident response begins before incidents occur:
- Data location inventory: Maintain current documentation of where personal data resides, including backup systems, archives, and temporary processing locations
- Notification decision trees: Create flowcharts mapping incident scenarios to notification requirements across applicable jurisdictions
- Template library: Develop pre-approved notification templates for supervisory authorities, individuals, and media (where required)
- Communication protocols: Establish clear escalation paths between security teams, privacy officers, legal counsel, executive leadership, and external advisors
- Forensic retainers: Pre-arrange relationships with privacy-specialized forensic firms capable of rapid personal data impact assessments
- Tabletop exercises: Conduct regular simulations testing both technical response and privacy notification procedures
4. Implement Privacy-by-Design Technical Frameworks
Privacy-by-design transforms privacy from a compliance checkbox into an architectural principle embedded in system development, procurement, and operations.
Technical Privacy Principles
Data Minimization: Collect, process, and retain only personal data necessary for specified purposes
- Technical implementations: Automated data purging based on retention policies, progressive profiling limiting initial data collection, need-to-know access controls, aggregation and anonymization in analytics systems
Purpose Limitation: Process personal data only for documented, legitimate purposes
- Technical implementations: Purpose-tagging in databases, consent management platform integration, access controls tied to processing purposes, automated blocking of repurposing attempts
Storage Limitation: Retain personal data only as long as necessary for processing purposes
- Technical implementations: Automated deletion workflows, retention policy engines, archive and destruction logging, backup lifecycle management
Security as Default: Apply appropriate security measures proactively, not reactively
- Technical implementations: Encryption by default, secure configuration baselines, automated vulnerability scanning, security requirements in procurement
Privacy-Enhancing Technologies (PETs)
Modern PETs enable data utility while minimizing privacy risks:
Differential Privacy: Adding mathematical noise to datasets ensuring individual records cannot be identified while preserving statistical accuracy
- Use cases: Analytics platforms, AI training datasets, public data releases, research databases
- Implementation: Libraries like Google’s differential privacy library, OpenDP, or commercial platforms integrating differential privacy
Homomorphic Encryption: Processing encrypted data without decryption, enabling computation on sensitive data while maintaining confidentiality
- Use cases: Cloud analytics on sensitive health/financial data, secure multi-party computation, encrypted database queries
- Implementation: Microsoft SEAL, IBM HELib, Palisade for homomorphic encryption schemes
Secure Multi-Party Computation: Multiple parties jointly compute functions over their inputs while keeping those inputs private
- Use cases: Cross-organizational analytics, fraud detection across financial institutions, collaborative research
- Implementation: SPDZ protocol implementations, Sharemind, or commercial secure computation platforms
Tokenization: Replacing sensitive data with non-sensitive substitutes (tokens) that maintain data utility without exposing original values
- Use cases: Payment processing, database security, format-preserving data protection
- Implementation: Vault technologies, payment tokenization standards (EMV), format-preserving encryption
Zero-Knowledge Proofs: Proving possession of information without revealing the information itself
- Use cases: Authentication, credential verification, compliance demonstration
- Implementation: zk-SNARKs, zk-STARKs, Bulletproofs in blockchain and identity systems
Integrating Privacy-by-Design Into Development Lifecycles
Secure Development Lifecycle (SDL) with Privacy:
- Requirements Phase: Privacy Impact Assessments identify legal obligations; translate into technical requirements
- Design Phase: Privacy architecture review ensures controls address identified risks; privacy patterns selected
- Implementation Phase: Code scanning for privacy violations (hardcoded PII, insecure storage); privacy-specific testing
- Testing Phase: Privacy test cases validating consent management, access controls, deletion capabilities, data export
- Deployment Phase: Privacy configuration validation, consent mechanism verification, data flow confirmation
- Operations Phase: Ongoing privacy monitoring, data protection impact assessments for changes, privacy incident response
Procurement and Vendor Management:
When selecting third-party systems or services, evaluate:
- Data processing agreements (DPAs) meeting GDPR Article 28 processor requirements
- Certifications (SOC 2 Type II, ISO 27701, ISO 27001, privacy-specific attestations)
- Subprocessor practices and notification procedures
- Data location and transfer mechanisms
- Security assessment rights and incident notification procedures
- Data deletion and return capabilities at contract termination
5. Establish Continuous Compliance Monitoring and Validation
Privacy regulations increasingly emphasize ongoing compliance demonstration, not point-in-time audits. Continuous monitoring provides early warning of compliance drift and regulatory readiness.
Automated Compliance Monitoring Framework
Technical Control Validation:
- Encryption verification: Automated testing confirming all personal data repositories maintain required encryption (at rest and in transit)
- Access control auditing: Regular review of who has access to personal data systems, validating against role-based access control (RBAC) policies and principle of least privilege
- Log completeness checks: Monitoring ensuring audit logging captures all required privacy-relevant events
- Backup security assessment: Validating backups receive equivalent security protections as production systems
Privacy Control Effectiveness:
- Data retention compliance: Automated scanning identifying personal data exceeding retention periods
- Consent validity monitoring: Tracking consent expiration, withdrawal, and scope to block processing without valid legal basis
- Cross-border transfer validation: Monitoring data flows for unauthorized transfers violating GDPR Chapter V or CPRA requirements
- Subject rights response metrics: Tracking time-to-completion for access requests, deletion requests, and correction requests against regulatory deadlines
Vulnerability and Patch Management:
- CVE monitoring: Tracking Common Vulnerabilities and Exposures affecting systems processing personal data
- Patch deployment timelines: Ensuring critical vulnerabilities in personal data systems receive accelerated patching
- Configuration drift detection: Identifying security configuration changes potentially weakening privacy protections
Compliance Metrics and KPIs
Establish quantitative measures demonstrating ongoing compliance:
Subject Access Request Fulfillment: Target <30 days (GDPR Article 15, CCPA/CPRA §1798.110)
Encryption at Rest Coverage: Target 100% (GDPR Article 32, CCPA reasonable security)
Encryption in Transit Coverage: Target 100% (HIPAA §164.312(e)(1), PCI DSS Requirement 4)
DPIA Completion Time: Target <14 days (GDPR Article 35)
Processors with Valid DPAs: Target 100% (GDPR Article 28)
Annual Privacy Training Completion: Target 100% (GDPR Article 32, HIPAA §164.308(a)(5))
Breach Notification Timeline: Target <72 hours (GDPR Article 33)
Code Privacy Security Scan Pass Rate: Target >95% (Privacy-by-design requirements)
Retention Policy Violations: Target 0 (Storage limitation principles)
Unauthorized Cross-Border Transfers: Target 0 (GDPR Chapter V, CPRA restrictions)
Third-Party Risk Continuous Assessment
Vendor security and privacy postures change over time. Implement continuous vendor risk monitoring:
- Automated security questionnaire updates: Annual or upon-material-change reassessments
- Breach notification monitoring: Tracking vendor security incidents affecting shared personal data
- Certification tracking: Validating vendor certifications remain current (SOC 2 reports, ISO certifications)
- Subprocessor change notifications: Reviewing and approving new subprocessors handling personal data
- Contractual compliance auditing: Exercising audit rights verifying vendor DPA compliance
6. Integrate Privacy Governance With Security Operations
The organizational structure separating privacy and security functions creates coordination gaps that lead to compliance failures. Integrated governance ensures privacy requirements inform security decisions and security capabilities enable privacy compliance.
Cross-Functional Privacy-Security Governance
Establish Integrated Governance Bodies:
- Privacy-Security Steering Committee: Joint leadership from CISO, DPO/Privacy Officer, Legal, Compliance, and Risk Management
- Meeting frequency: Monthly strategic meetings, weekly operational coordination during projects or incidents
- Responsibilities: Approve privacy-security frameworks, resolve conflicting requirements, allocate resources, oversee cross-functional initiatives
Shared Accountability Framework:
Data Classification
- Privacy: Define personal data categories and sensitivity levels
- Security: Implement technical classification controls
- Shared: Validate classification accuracy and coverage
Access Controls
- Privacy: Specify role-based access aligned with processing purposes
- Security: Implement identity and access management systems
- Shared: Regular access reviews and recertification
Encryption
- Privacy: Identify data requiring encryption per regulations
- Security: Select and implement encryption technologies
- Shared: Key management and rotation procedures
Incident Response
- Privacy: Assess privacy impact and notification requirements
- Security: Contain, investigate, and remediate incidents
- Shared: Joint notification decisions and communications
Vendor Management
- Privacy: Negotiate DPAs and privacy terms
- Security: Conduct security assessments
- Shared: Joint vendor risk ratings and decisions
Training
- Privacy: Develop privacy awareness content
- Security: Develop security awareness content
- Shared: Deliver integrated privacy-security training
Operationalizing Privacy Requirements in Security Workflows
Change Management Integration:
All system changes affecting personal data processing trigger both security and privacy reviews:
- Security assessment: Vulnerability introduction, attack surface changes, control effectiveness impact
- Privacy assessment: Legal basis adequacy, purpose limitation compliance, individual rights impact, potential for new DPIA requirement
- Joint approval: Both privacy and security sign-off required before implementation
Security Tool Configuration for Privacy:
- SIEM configuration: Create privacy-specific correlation rules detecting unauthorized personal data access, bulk exports, unusual query patterns against personal data repositories
- DLP (Data Loss Prevention): Configure policies protecting personal data categories (PII, PHI, financial data) with distinct handling for different sensitivity levels
- CASB (Cloud Access Security Broker): Enforce privacy policies in cloud applications, blocking unauthorized cloud storage of personal data, enforcing encryption requirements
- IAM (Identity and Access Management): Implement least privilege access to personal data, separate administrative credentials from personal data access, enforce MFA for personal data systems
Privacy Automation in Security Operations:
- Automated data discovery: Regular scanning identifying new personal data repositories requiring security and privacy controls
- Policy enforcement automation: Technical controls automatically applying encryption, access restrictions, and retention policies based on data classification
- Compliance reporting automation: Dashboards providing real-time compliance status across multiple regulatory frameworks
- Incident privacy triage: Automated assessment estimating personal data exposure severity to prioritize response and notification obligations
Building Privacy-Security Culture
Technical controls fail without organizational commitment to privacy as a security imperative:
- Integrated training programs: Eliminate separate privacy and security training; deliver unified content showing how security protects privacy and privacy requirements drive security
- Privacy champion networks: Embed privacy expertise within security teams and security expertise within privacy teams
- Incident lessons learned: Analyze both security incidents and privacy violations, sharing findings across both functions
- Continuous improvement cycles: Regular retrospectives examining how privacy-security integration can be strengthened
Proactive Compliance: The CaptainCompliance.com Superhero Philosophy
The technical frameworks outlined above share a common principle: proactive compliance is significantly more cost-effective than reactive remediation. Organizations implementing privacy-compliant security architecture from inception avoid:
Regulatory fines: GDPR fines reached €2.92 billion through 2023; U.S. state privacy law enforcement is accelerating with millions in penalties already assessed
Breach notification costs: IBM’s 2025 Cost of a Data Breach Report identifies average breach costs of $4.44 million down from $4.88 million the year before, with regulated industry costs significantly higher
Retrofit expenses: Implementing privacy controls post-deployment costs 10-100x more than privacy-by-design approaches
Reputational damage: Privacy violations erode customer trust, reducing lifetime value and acquisition effectiveness
Operational disruption: Reactive compliance often requires system shutdowns, rushed audits, and emergency remediation diverting resources from strategic initiatives
The proactive alternative—building cybersecurity programs that inherently meet privacy regulations—transforms compliance from a cost center into strategic advantage. Organizations demonstrating mature privacy-security integration differentiate themselves in privacy-conscious markets, streamline procurement cycles with enterprises requiring vendor privacy commitments, and avoid the competitive disadvantages of public privacy failures.
This comprehensive, proactive approach doesn’t just check compliance boxes—it builds resilient, trustworthy systems that protect individuals’ fundamental rights while enabling responsible data innovation.
Implementation Roadmap
Organizations beginning privacy-compliant cybersecurity program development should follow this phased approach:
Phase 1 (Months 1-3): Foundation and Assessment
- Conduct comprehensive data mapping identifying all personal data processing
- Complete gap analysis comparing current security controls against privacy regulatory requirements
- Establish privacy-security governance structure and integrated steering committee
- Document current state privacy-security maturity
Phase 2 (Months 4-6): Priority Control Implementation
- Implement privacy-compliant logging and audit trail capabilities
- Establish encryption at rest and in transit for all personal data repositories
- Deploy data classification system tagging personal data categories
- Develop privacy-aware incident response procedures
Phase 3 (Months 7-9): Advanced Capabilities and Automation
- Implement automated compliance monitoring and validation
- Deploy privacy-enhancing technologies appropriate for use cases
- Establish continuous vendor risk assessment processes
- Integrate privacy requirements into development lifecycles
Phase 4 (Months 10-12): Optimization and Maturity
- Refine controls based on effectiveness metrics
- Expand privacy-by-design across all technology initiatives
- Achieve industry-recognized privacy-security certifications (ISO 27701, SOC 2 Type II)
- Conduct independent privacy-security audit validating regulatory compliance
Ongoing: Maintain compliance through continuous monitoring, regular assessments, training updates, and adaptation to evolving regulatory requirements.
Take Action: Your Path to Privacy-Compliant Security
Building cybersecurity programs that meet privacy regulations requires more than adding privacy controls to existing security architectures. It demands fundamental integration: security architectures designed around personal data protection principles, privacy assessments driving security implementations, incident response satisfying both technical and regulatory imperatives, and governance structures unifying privacy and security functions.
The technical complexity of satisfying GDPR, CCPA/CPRA, HIPAA, state privacy laws, and international regulations simultaneously can appear overwhelming. However, organizations applying the six strategic pillars outlined in this guide—evidence-generating controls, data-flow-driven architecture, privacy-aware incident response, privacy-by-design frameworks, continuous compliance monitoring, and integrated governance build programs that satisfy multiple regulatory frameworks efficiently while establishing resilient security postures.
The choice between reactive compliance and proactive privacy-security integration ultimately determines whether organizations view privacy regulations as burdensome constraints or opportunities to build competitive advantages through trustworthy data practices. The organizations thriving in today’s regulatory environment have chosen the latter path, embedding privacy protection into their security DNA rather than bolting it on after the fact.
The roadmap is clear. The frameworks are established. The technology exists. What remains is organizational commitment to building cybersecurity programs that don’t just prevent breaches they demonstrably protect the fundamental privacy rights of individuals whose data organizations process. That’s not just good compliance.
It’s good business and you’ll be rewarded for respecting your data subjects privacy rights and security with the help of Captain Compliance!