You don’t respond to a Data Subject Access Request (DSAR) with a file dump and a shrug. You respond with clarity, lawful precision, and evidence that your systems do exactly what your privacy notice promised. This long-form guide gives you a proven DSAR response letter structure, ready-to-send templates, and an operational playbook you can plug into your ticketing system today or if you book a demo with us we can show you how we can automate your data subject requests as they come in. We also explain why inbound request volumes are rising (hello, PrivacyHawk, Aura, Cloaked, and Optery), how to verify identity without over-collecting, when to deny or narrow a request, and how to automate the whole workflow.
What Is a Data Subject (or Consumer) Request?
A Data Subject Request (also called a “consumer request” in some U.S. state laws) or “Subject Rights Request”is a formal ask from an individual or their authorized agent to exercise statutory privacy rights. The exact rights vary by jurisdiction, but the common core includes:
- Access / Know: confirmation that you process their personal data and a copy or clear summary.
- Delete: erase personal data, subject to legal exceptions.
- Correct / Rectify: fix inaccurate personal data.
- Restrict processing (GDPR/UK GDPR): pause most processing while retaining the data.
- Opt out of sale or sharing for cross-context behavioral advertising (various U.S. state laws).
- Limit the use of sensitive personal information (e.g., certain U.S. states).
- Portability: receive data in a structured, commonly used, machine-readable format.
- Contest automated decision-making where a decision is made solely by automation and has legal or similarly significant effects (e.g., credit, employment).
Response clocks (typical): GDPR/UK GDPR require a response within one month (with a possible two-month extension for complexity/volume). Many U.S. state laws provide 45 days (with a possible 45-day extension). Always confirm your applicable jurisdiction requirements.
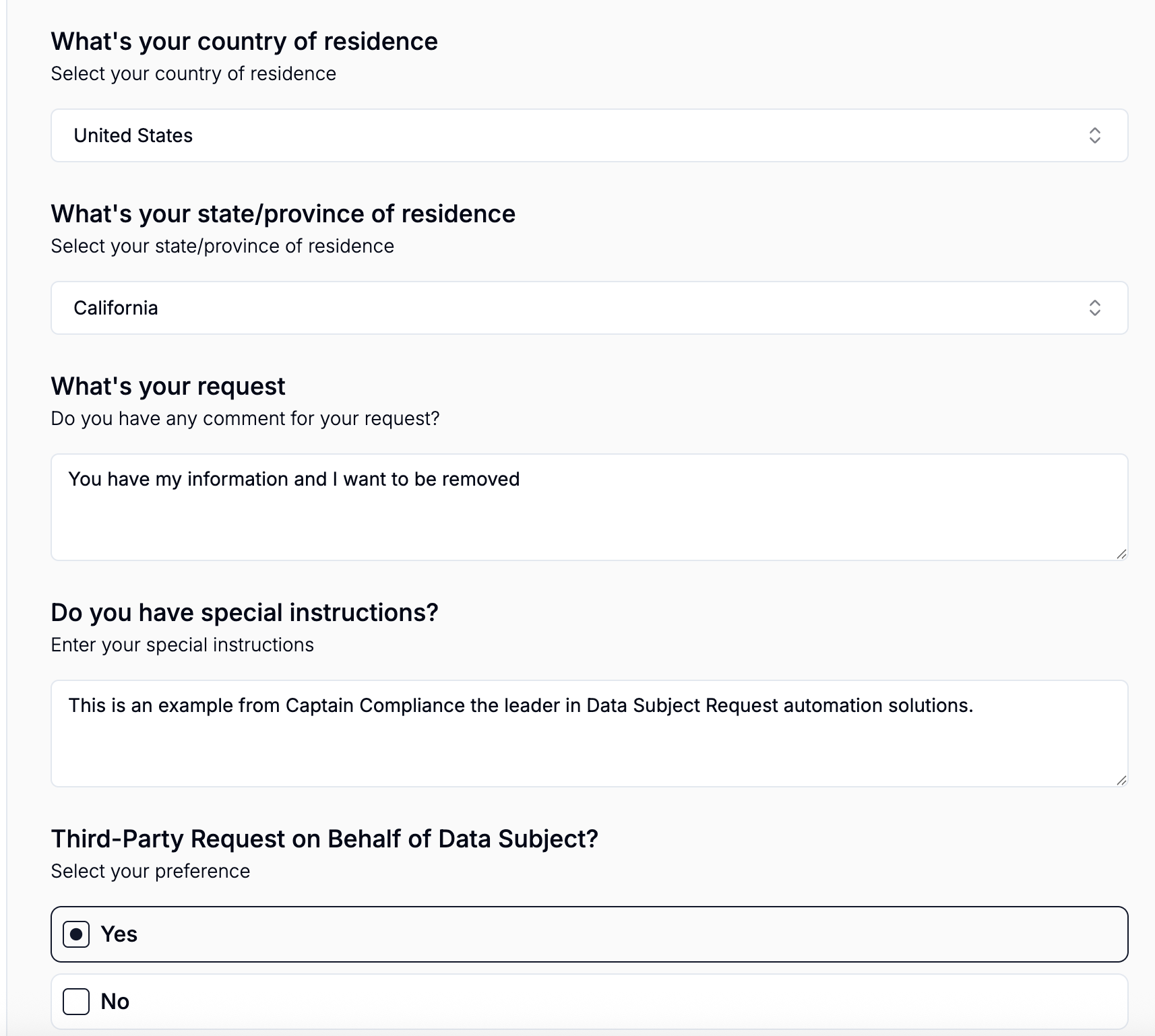
How Consumer Tools Democratized DSARs—And Why Your Queue Is Growing
A wave of consumer privacy tools is making it simple for everyday people to send rights requests or demand removals. If you’ve noticed a huge increase in requests buckle up because its only going to explode from here. Companies like Privacy Hawk have found the top 12,000 websites and have made it as simple as clicking to go through and make requests to opt out and send out a DSAR. This has made it so that response letters and knowing how to respond to a subject rights request is extremely important and if you can automate them with Captain Compliance’s DSAR software even better. These are the companies behind those increasing number of Subject Rights Requests:
- Optery: automates opt-outs and deletions across hundreds of data brokers and provides step-by-step guides.
- PrivacyHawk: a mobile/web app that scans for companies holding a user’s data and sends removal/opt-out requests, with tracking.
- Aura: identity-protection suite that includes data broker removal and ongoing re-submission.
- Cloaked: takes a proactive approach by generating masked emails/phones/addresses so less personal data is collected in the first place.
Operational impact: expect more standardized requests, more authorized-agent submissions, and more “remove me everywhere” instructions—even when you’ve never had direct contact with the requester (e.g., broker feeds, adtech IDs). Your intake and verification flows must scale gracefully.
What Kinds of DSARs Your Business Can Receive
Below are the most common DSAR “flavors,” what they require, and response tips.
Access / “Request to Know”
Provide confirmation that you process the individual’s data plus either a copy or a structured, human-readable summary. Include purposes, categories, sources, recipients, and retention/criteria. If disclosing a full copy would expose trade secrets or others’ data, provide a redacted copy or a meaningful summary.
Deletion (Erasure)
Delete or de-identify personal data unless a legal exception applies (e.g., tax retention, security logs, exercising or defending claims). Be explicit about partial denials and what you did remove. Document backup handling (e.g., deletion upon next normal rotation of immutable backups).
Correction (Rectification)
Update demonstrably inaccurate fields (e.g., profile attributes, contact info). Keep an audit trail of what was changed, when, and by whom. Where you rely on third-party sources, note the source and sync cadence.
Restriction of Processing
Pause non-essential processing while keeping the data. Continue only what’s strictly necessary (compliance, security, prevention of fraud). Confirm when restriction begins, which activities will pause, and how long restriction will last.
Opt-Out of Sale/Sharing
Stop data flows used for cross-context behavioral advertising and any “sale” as defined by law. Honor browser-based opt-out preference signals (e.g., Global Privacy Control) and propagate them to known accounts where feasible.
Limit the Use of Sensitive Personal Information
Limit processing of sensitive categories (e.g., precise geolocation, biometrics) to necessary purposes or those explicitly permitted by law. Reflect these limits in vendor and product configurations.
Portability
Provide a machine-readable export (commonly CSV or JSON) that is reasonably usable by the requester. Include a brief data dictionary so column names are meaningful.
Contest Automated Decision-Making
When a legally or similarly significant decision was made solely by automation, the individual may request human review, an explanation at a high level, and a chance to express their views. Map a clear path for escalation to qualified reviewers.
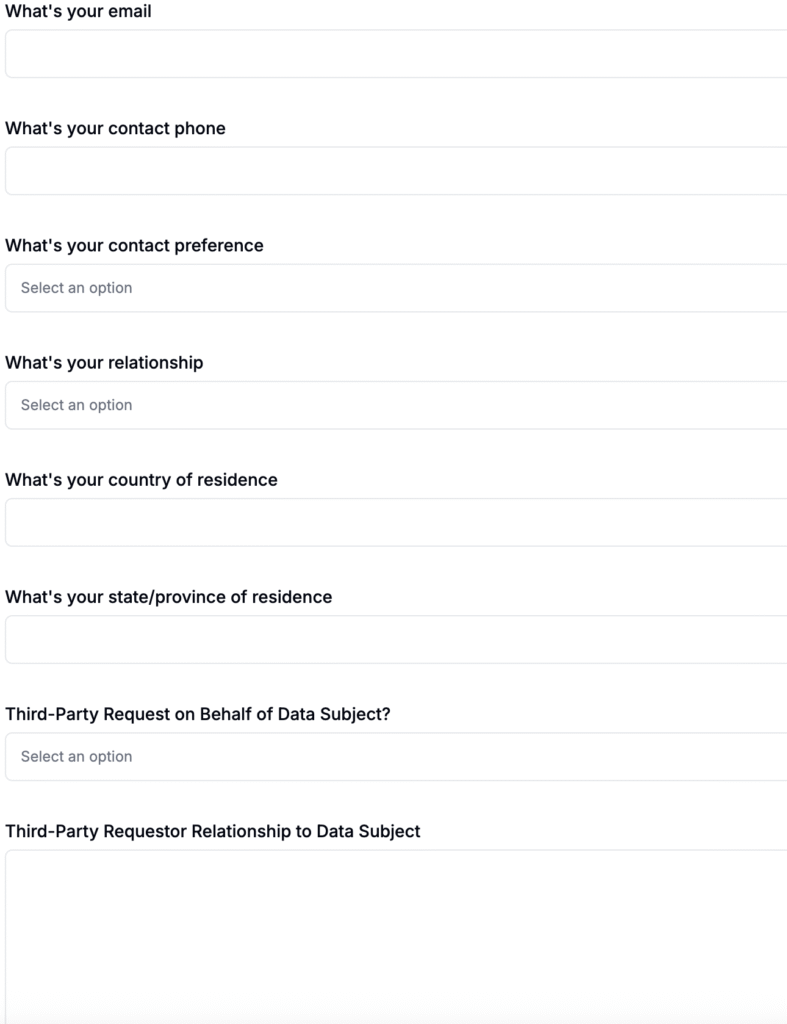
Requirements to Act: Timeframes, Verification, Rejections & Duplicates
Timeframes You Must Hit
- GDPR/UK GDPR: one month from receipt; extend up to two months for complexity/volume (notify within the first month with reasons).
- Many U.S. state laws: 45 days; extend once for 45 more days when reasonably necessary (notify within the first 45 days with reasons).
Build SLA timers into your ticketing system and design timeouts for every handoff (security, data engineering, counsel). Missed deadlines are low-hanging fruit for regulators and plaintiffs. If you’re using our DSAR software then you will have automatic timers and notices so you can abide by the privacy laws in whichever jurisdiction the responder if coming from.
Identity Verification (Without Over-Collecting)
Verification must be reasonable and proportionate. Don’t default to requesting IDs. Start with the lowest-friction method that still protects the user:
- Prefer logged-in, in-product requests.
- Use known contact points (e.g., send a one-time magic link to the email on file).
- For non-account contexts, match two data points you already hold (e.g., order number + last login month).
- Escalate only for sensitive disclosures (e.g., require a third data point or short-lived ID check).
- Store any verification evidence briefly, segregated from production, and delete promptly.
Duplicates, Excessive or Manifestly Unfounded Requests
You may decline or charge a reasonable fee for manifestly unfounded or excessive requests (e.g., abusive frequency). Many U.S. state laws cap the number of free responses per year. If you refuse or narrow a request, give a written explanation and, where required, an appeal path and timeline.
DSAR Templates (Copy, Paste, Personalize)
The following templates are deliberately plain. Swap bracketed items and adjust jurisdictional statements to match the law that applies to you. If you setup an account with Captain Compliance we can handle all of this process for you vs. having a plain privacy@ email that may blend in with the rest of the email requests your company may be receiving.
A. Acknowledgment & Identity Verification
Subject: We’ve Received Your Privacy Request — Ticket [ID]
Hi [Name],
Thanks for contacting [Company] about your privacy rights. We’ve opened ticket [ID]
for the following request(s): [access / delete / correct / restrict / opt-out /
limit sensitive info / portability / contest automated decision].
To protect your privacy, we need to verify your identity. Please reply from the
email associated with your [Company] account and confirm TWO of the following:
• Your account username (if applicable)
• Last transaction month/year OR last login month/year
• The phone number on your account (if applicable)
If you don’t have an account, share the email(s) you used with us and the
approximate month/year of your last interaction.
Once verified, we’ll respond within [one month / 45 days] as required by law.
Best regards,
[Privacy Team Name]
[Contact + secure upload link]B. Identity Unverifiable — Narrow Ask
Subject: We Need a Bit More to Complete Your Request — Ticket [ID]
Hi [Name],
We’re having trouble verifying your identity with the information provided. To
protect your privacy, we cannot disclose data until we’re sure the request is
from you (or your authorized agent).
Please provide ONE of the following:
• An order number from any purchase, OR
• The last four digits of the phone number on your account, OR
• A reply from the email you used with [Company].
If you prefer not to share these, we can:
• Apply an opt-out of sale/sharing to your browser/device where supported, and
• Add your identifiers to our marketing suppression list.
If we don’t hear back within [X] days, we may close this ticket as “unable to verify.”
You can reopen anytime with the details above.
Thanks,
[Privacy Team]C. Completion — Access + Portability
Subject: Your Privacy Request Is Complete — Ticket [ID]
Hi [Name],
We completed your [access/portability] request. Below is a human-readable summary.
We’ve also provided a machine-readable export (“[Name]_export_[date].zip”) with
CSV/JSON files and a data dictionary.
WHAT WE HAVE ABOUT YOU
• Identifiers: [email(s), account ID(s), device/cookie IDs if linked to your account]
• Account & activity: [dates, features used, session counts]
• Transactions: [dates, amounts, last four digits only if applicable]
• Marketing interactions: [subscriptions, campaign responses]
• Support history: [ticket dates/subjects; redactions applied to protect third parties]
WHY WE HAVE IT (purposes)
[service delivery; security/fraud prevention; compliance; support; marketing (consent-based)]
SOURCES
[you; your devices/browsers; service providers]
SHARING/DISCLOSURE
[processors like cloud hosting, payments, email; sale/sharing: [not applicable OR ceased on (date)]]
RETENTION
[brief summary of retention]
If anything is inaccurate, reply with the correction and context and we’ll fix it.
Regards,
[Privacy Team]D. Completion — Deletion
Subject: Your Deletion Request Is Complete — Ticket [ID]
Hi [Name],
We deleted or de-identified your personal information from our production systems
associated with: [emails/phones/account IDs].
WHAT THIS MEANS
• Removed from: [systems list].
• Retained only what law requires (e.g., tax, security logs) and will delete after retention ends.
• Immutable backups will cycle out within [X] days.
If you return later, we’ll treat you as a new user unless you ask us to restore
any retained preferences.
Regards,
[Privacy Team]E. Completion — Correction/Rectification
Subject: Your Correction Request Is Complete — Ticket [ID]
Hi [Name],
We’ve updated the following fields:
• [Field A]: [old value] → [new value]
• [Field B]: [old value] → [new value]
We also notified relevant service providers so their records will align during
their next sync. If anything else needs attention, reply to this email.
Regards,
[Privacy Team]F. Restriction of Processing Confirmed
Subject: Processing Restricted — Ticket [ID]
Hi [Name],
We have restricted processing of your personal information as requested. During
this period we will process your data only for necessary purposes (e.g., security,
fraud prevention, legal obligations). We will not use your data for marketing or
other non-essential activities while the restriction is in place.
Restriction begins: [date]
We’ll notify you before lifting the restriction or if further action is required.
Regards,
[Privacy Team]G. Opt-Out of Sale/Sharing Applied
Subject: Your Opt-Out Preferences Are Active — Ticket [ID]
Hi [Name],
We have applied your opt-out of sale/sharing for cross-context behavioral
advertising. We also honor valid opt-out preference signals from your browser
(e.g., Global Privacy Control) and apply them to any known account.
Note: You may still see generic ads that are not based on your personal data.
Regards,
[Privacy Team]H. “No Matching Records Found” + Ad Opt-Out
Subject: We Couldn’t Find Records — Here’s What We Did Next
Hi [Name],
We searched for [emails/phones] and did not find records we can link to you in
our systems.
To respect your preferences, we have:
1) Applied an opt-out of sale/sharing to your browser/device where supported, and
2) Added your identifiers to our suppression list to prevent future marketing profiles.
If you have other identifiers we should search (e.g., prior emails, phone numbers),
reply and we’ll re-run the search.
Regards,
[Privacy Team]I. Extension Notice
Subject: We Need More Time — Ticket [ID]
Hi [Name],
We’re working on your request but need more time due to [complexity/volume].
We will complete your request by [new due date] and will keep you informed.
Thanks for your patience,
[Privacy Team]J. Rejection (Jurisdiction / Verification / Excessive / Exemptions)
Subject: We Can’t Complete Your Request — Here’s Why + Your Options
Hi [Name],
We reviewed your request [ID]. We’re unable to complete it because:
• Lack of jurisdiction: [Company] is not subject to the law cited (e.g., requester
is not a covered resident or we do not meet statutory thresholds), OR
• Unable to verify identity with the information provided, OR
• Manifestly unfounded/excessive (e.g., repetitive), OR
• Exempt data (e.g., legal holds, security logs, trade secrets, or truly de-identified data).
If applicable, you may appeal by replying with “Appeal” in the subject within [X] days.
We will respond within [Y] days with a written decision.
Thanks,
[Privacy Team]K. Appeal Response (If Your Law Requires an Appeal Process)
Subject: Decision on Your Appeal — Ticket [ID]
Hi [Name],
We reviewed your appeal. Decision: [Upheld / Overturned].
Rationale: [plain-language explanation].
If we overturned, the next steps are: [verification / fulfillment plan & timeline].
If we upheld, you may have the right to complain to [regulator name/URL].
Regards,
[Appeals Reviewer]Request Completion Response Examples
A. Access Summary Table (Inline)
| Category | What We Hold | Purpose | Source | Sharing/Disclosure | Retention |
|---|---|---|---|---|---|
| Identifiers | Email(s), account ID(s) | Account, security | You | Cloud hosting, fraud tools | [X] months |
| Usage | Session counts, feature usage | Service delivery, reliability | Device/browser | Analytics (processor) | [Y] months |
| Transactions | Dates, amounts, last4 | Fulfillment, tax | You / payment processor | Payment provider | [Z] years (legal) |
| Marketing | Subscriptions, campaign responses | Comms you requested | You | Email service (processor) | [W] months |
| Support | Ticket dates/subjects (redacted) | Customer support | You | Support desk (processor) | [V] months |
B. Portability Package (Suggested ReadMe.txt)
FILES
• profile.csv (account_id, email, created_at, last_login_at)
• preferences.csv (account_id, preference_key, value, updated_at)
• transactions.csv (account_id, order_id, date, amount, last4)
• support_cases.csv (case_id, subject, opened_at, closed_at, redacted_summary)
NOTES
• Timestamps are ISO 8601 (UTC).
• Currency amounts are in [currency].
• Redactions applied where disclosure would reveal third-party info or trade secrets.C. Deletion Confirmation
- Removed from: CRM, marketing platform, analytics (user-level), support desk, data warehouse extracts.
- Retained: tax/transaction records and security logs (for [N] years) as required by law.
- Backups: immutable backups will cycle out within [X] days; we do not access backups except for disaster recovery.
- Vendors: deletion or suppression instructions sent to [list of processors].
Types of Fields Your DSAR Form Can Ask For (Keep It Minimal)
- Request type(s): access, delete, correct, restrict, opt-out, limit sensitive, portability, contest ADM.
- Primary identifier: email (required) and any other emails used with you; optional phone number if used for the account.
- Context: date range, products/services used; whether this is an authorized agent or parent/guardian submitting.
- Delivery preference: secure portal or email; portability format (CSV/JSON).
- Security: logged-in submission preferred; if not logged in, plan a two-factor challenge after submission.
Do not ask for government ID by default. Escalate to ID only if proportional and necessary to prevent unauthorized disclosure. If you followed our warnings about the Honda Enforcement action over asking for too much information this led to a $632,500 fine, Healthline, and retailer Todd Snyder in California also had a similar issue when the CPPA fined them over a CCPA violation.
What If No Result Is Found? How to Respect Choices and Opt Them Out of Targeted Ads
Sometimes your search comes up empty. That doesn’t end the conversation. If you can’t link the person to records:
- Explain what systems and identifiers you searched.
- Honor universal signals: detect and act on opt-out preference signals (e.g., Global Privacy Control) for the browser/device and any known account.
- Add to suppressions: create or append to a hashed suppression list for the provided identifiers.
- Educate: give pointers to browser and OS ad settings and industry opt-out tools (e.g., NAI/DAA) so the person can reduce cross-app tracking elsewhere.
Rejection Reasons (Say “No” Without Burning Trust)
- Lack of jurisdiction: the requester is not a covered resident or the entity doesn’t meet thresholds under the cited law.
- Unable to verify identity: evidence insufficient and disclosure would risk unauthorized access.
- Manifestly unfounded or excessive: harassing or repetitive requests beyond statutory caps.
- Exempt data: legal holds, security logs, privileged materials, trade secrets, or truly de-identified data (no duty to re-identify).
Every denial should include a plain-language reason, a lawful basis, and—if required—an appeal path (with timeline). Offer a path to resubmit with better verification or a narrowed scope.
How to Automate DSARs and Where Captain Compliance Helps!
Manual DSARs don’t scale. Here’s an automation blueprint you can adapt in any stack; the items in parentheses are modules we can help you deploy quickly or you can let us integrate and setup your DSAR
- Intake: a secure web form with CAPTCHA, rate-limits, and logged-in preference (Intake+).
- Verification: rules engine for low/medium/high assurance; SSO hooks; magic-link email; OTP SMS where appropriate (Verify).
- Routing: auto-tag by jurisdiction and request type; set SLA timers and extension counters (SLA Guard).
- Discovery connectors: CRM, data warehouse, marketing, support, payment, cloud logs; standardized export adapters (Discovery Hub).
- Redaction: automated PII scrubbing for free-text; human QA for edge cases (Redactor).
- Portability exporter: schema-versioned CSV/JSON bundles + ReadMe (Portability Export).
- Opt-out engine: sets first-party flags, honors GPC, writes to adtech suppression endpoints, and notifies vendors (GPC / Adtech Suppression).
- Appeals workflow: second-level queue with a clear decision letter and timeline (Appeals Desk).
- Evidence pack: one-click export of correspondence, verification steps, queries, redactions, and final deliverables for audits/regulators (Audit Kit).
Data Subject Access Request FAQs
How long do we have to respond?
GDPR/UK GDPR: one month (extend up to two months for complexity/volume). Many U.S. state laws: 45 days (extend once for 45 days when reasonably necessary). Notify the requester within the initial window if you need more time.
What happens if we reject a request?
Provide a written explanation, cite the lawful basis, and—where required—offer an appeal path with a timeline. Keep the door open for re-submission with better verification or a narrowed scope.
What do we need to verify a request?
Use proportionate methods. Prefer logged-in submission, magic-link email, or matching two data points already on file. Escalate to stronger evidence only for sensitive disclosures. Avoid collecting new sensitive IDs unless necessary, and store any evidence briefly and separately.
What are we required to disclose for access?
Confirmation of processing, the data itself or a meaningful summary, plus purposes, categories, sources, recipients, retention/criteria, and rights. Redact data where disclosure would reveal trade secrets or others’ personal information.
Do we have to honor Global Privacy Control (GPC)?
If the law that applies to you recognizes opt-out preference signals, you must detect and honor qualifying signals as a request to opt-out of sale/sharing for the browser/device and, where feasible, apply to associated accounts.
How many times must we respond for free?
Rules vary. GDPR generally requires free responses unless a request is manifestly unfounded or excessive. Some U.S. state laws provide a set number of free responses per year. Check your applicable statute.
What about automated decisions?
For legally or similarly significant decisions made solely by automation, provide a path to human review, a high-level explanation, and a way for the individual to express their views and contest the outcome.
What if data is de-identified or only in backups?
You typically are not required to re-identify truly de-identified data to respond. For immutable backups, document that deletion will occur on the next normal rotation; do not restore backups solely to process a DSAR.
How do we handle authorized agents or parents/guardians?
Verify both the identity of the subject and the authority of the agent/guardian with proportionate documentation (e.g., signed authorization, power of attorney, proof of parentage), then process as normal.
Do we need to update our privacy notice?
Yes—your notice should reflect intake channels, verification methods, what you disclose, timelines, appeal options, and how you honor opt-out signals. Keep it readable and consistent with what your code actually does.
A One-Page DSAR Checklist if Handling Manually (We recommend you use Captain Compliance’s Leading DSAR Software Solution)
- Acknowledge (Day 0–3).
- Verify identity/authority (proportionate).
- Scope (types, identifiers, date range, jurisdiction).
- Discover (systems & processors; include vendors).
- Redact (third-party data, trade secrets).
- Assemble (summary + CSV/JSON portability bundle).
- Deliver securely (portal with expiring link; separate password if email).
- Log & close (deadlines met; evidence pack saved).
- Appeal path (where required).
- Feed improvements to engineering and vendor management.
A Great Data Subject Rights Request Response
A great DSAR response isn’t a PDF—it’s a proof of governance. You show that your toggles and promises work in code, that you can surface a person’s data without exposing someone else’s, and that you honor universal signals without making the user click through a maze. With a respectful letter, proportionate verification, and automated plumbing (discovery → redaction → portability export → opt-out enforcement), you’ll convert a regulatory obligation into a trust moment—and you’ll be ready when the next wave of requests lands from PrivacyHawk, Aura, Cloaked, Optery, or an authorized agent representing thousands of consumers that are going to abuse the DSAR system and lawyers are speaking out that firms like Swigart who files CIPA claims are catching onto the DSAR litigation opportunities.
So book a demo right away and work with Captain Compliance to automate your DSAR’s and follow the legal requirements.