Building a durable privacy program shouldn’t slow your business; it should power it. When privacy is engineered into your stack—lawful bases mapped, consent signals honored in code, retention automated, and vendor risk controlled—you reduce regulatory exposure and unlock higher-quality data for marketing and analytics. Captain Compliance combines expert consulting with software (consent and preference management, DSAR automation, deletion evidence, and many more privacy automation tools) to deliver outcomes that regulators, platforms, and customers trust. The result is a privacy program that pays for itself: faster approvals from legal and partners, fewer production incidents, better measurement in consent-constrained regions, and clearer documentation when questions arise. As your privacy program matures having the help & support of our recommended privacy attorneys, consultants, and our software will make everything seamless.

Schedule a 15-minute Demo with a Data Privacy Expert
What Is Data Privacy Consulting? (And Why It’s More Than Policies)
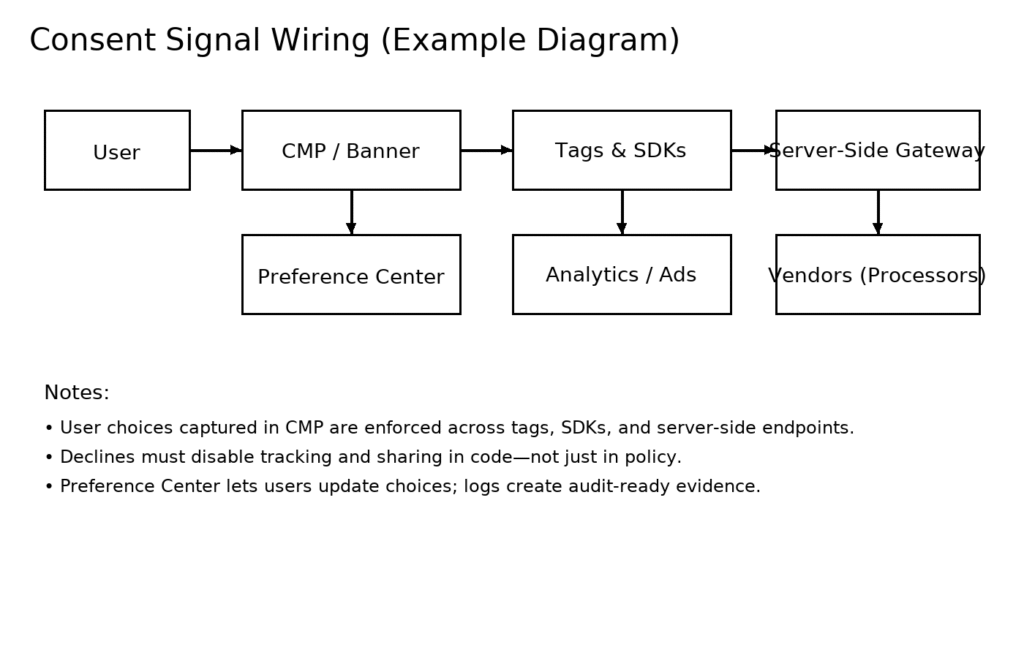
Data privacy consulting is the discipline of translating laws, platform rules, and customer expectations into a living operating system for your company’s data. It begins with simplified assessments internally or baseline questions such as: what personal data do we collect, why do we collect it, how long do we keep it, who touches it, and how do we prove all of that on demand—and ends with technical enforcement that matches the answers. A strong engagement maps each dataset to a lawful basis, defines purposes and limits, and then wires those decisions into the tools your teams actually use: consent banners and preference centers, tag managers, SDKs, server-side endpoints, data warehouses, customer support systems, and retention jobs. When done well, privacy consulting doesn’t produce binders; it produces working systems, trained humans, and evidence. This matters because the risks are now multi-directional. Regulators expect working consent and timely rights responses. Platforms require certified consent signals in parts of the world before they’ll deliver or measure ads. Customers judge brands by how transparent and responsive they are when a family member wants to opt out, delete a profile, or ask what data you hold. And internal teams need clear guardrails so marketing, product, and data science can move quickly without accidentally crossing lines. In practice, a consultant acts as your architect and general contractor: inventorying data flows, prioritizing quick wins, writing notices that match reality, and building the muscle for DSARs, vendor governance, and incident response. The measure of success is operational: fewer “can we do this?” meetings, faster time from idea to launch, and a smaller blast radius when something goes wrong. Most importantly, privacy consulting reframes the problem from “avoid fines” to “collect the right data, with consent, so it’s more valuable over time.” Consented data converts better, persists longer, and is easier to activate across channels. That is why the most effective programs are built to be audited and measured—not just once, but every quarter.
Business Outcomes vs. Checklists: What Great Privacy Consulting Delivers
Great privacy work moves three needles at once: risk, revenue, and speed. On the risk side, you get clarity on lawful bases, real consent enforcement, contracts that actually bind vendors, and deletion proof that reduces the cost of investigations and complaints. On the revenue side, you build consented audiences and preference-driven relationships that perform better than spray-and-pray tactics, while recovering measurement through privacy-safe modeling. And on speed, you replace one-off approvals with a repeatable process that lets product and marketing teams ship with confidence. Concretely, this looks like establishing a “from ad to cancel” journey where every claim and toggle is truthful and tested; deploying a consent management platform that supports standardized signals for the regions you serve; implementing a DSAR portal with identity verification that doesn’t create new ID copies; codifying retention so sensitive data self-purges without a calendar reminder; and standing up vendor governance with deletion SLAs, sub-processor transparency, and purpose limitation baked into the contract. It also means preparing for the bad day: tabletop exercises, first-72-hours playbooks, regulator and consumer templates, and evidence-preservation routines. But the difference between a checklist and a business outcome is instrumentation. We insist on logs and dashboards that prove declines shut off tags and server-side events, that DSARs hit their SLA, that deletion jobs ran as scheduled, and that consented audiences are growing. The point isn’t to collect screenshots; it’s to normalize a cadence of proof so compliance becomes a by-product of doing the right thing in the stack. Over time, this discipline compounds. Marketing spends less time negotiating platform requirements and more time optimizing creative for opted-in customers. Engineering reuses proven patterns for new features. Legal and security sleep better because decisions have traceable owners and artifacts. That is the real promise of privacy consulting: operationalizing trust so your teams can move faster with less drag.
Software Combined With Data Privacy Consulting
Companies don’t need more theory; they need working systems. Captain Compliance delivers both the brains and the tools to make privacy stick. Our approach pairs senior consultants with a product suite that includes consent and preference management, DSAR intake and fulfillment, automated retention and deletion evidence, and audit-ready logs that show exactly what was collected, who consented to what, and when data was erased. This software-enabled model shortens time-to-value because the essentials are already built: a consent banner and preference center that can be configured for each brand and region; standardized integrations that gate pixels, SDKs, and server-side events based on user choice; identity-safe DSAR verification flows; and reporting that satisfies everyone from marketing to auditors.
We meet you where you are—whether you run a simple web stack or a complex, multi-app environment—and we design for your stage. Startups get a rapid baseline: updated notices, a certified consent solution, a DSAR portal, and a retention plan that actually deletes. Scale-ups add vendor risk management, server-side enforcement, and quarterly evidence packs. Enterprises extend to global governance, cross-border transfer controls, and program reporting to executives and boards. Across all tiers, our differentiator is proof. We treat “decline” as a technical requirement, not copy on a button. We test that opt-outs cascade through tags, SDKs, and server-side endpoints. We document lawful bases dataset by dataset. We maintain a vendor registry that maps purposes, sub-processors, and deletion SLAs. And we produce deletion and consent evidence every quarter so you can respond to questions with facts. Because the software captures the artifacts, your team avoids spreadsheet fatigue and last-minute hunts for screenshots. The benefit shows up in growth as much as in audits: consented audiences that perform, cleaner signals for modeling, and fewer roadblocks when expanding into new regions or launching new channels.
0–90 Day Methodology Privacy Sprint
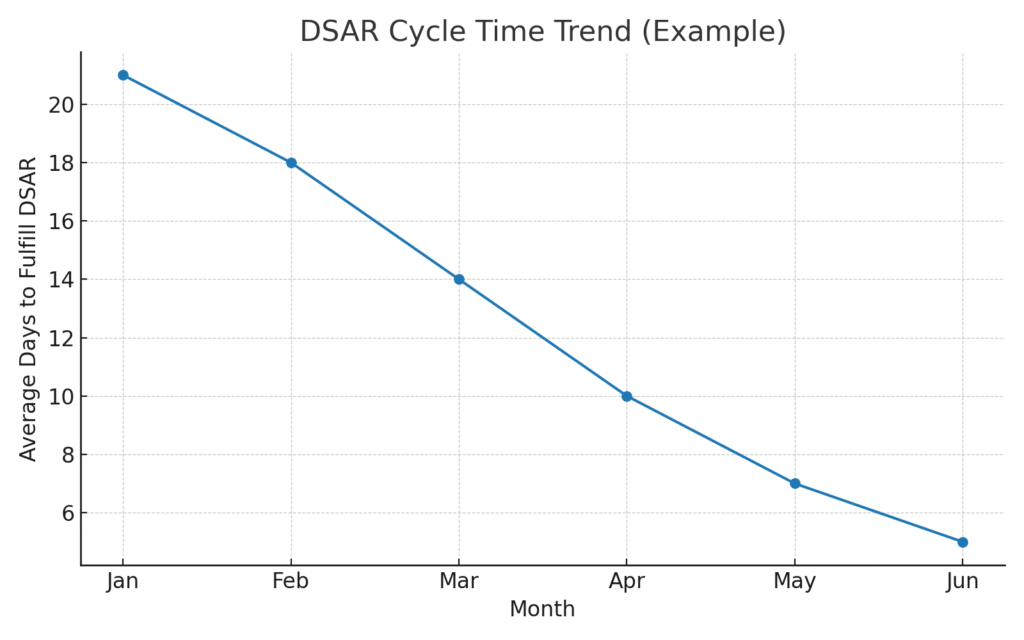
We have a database of the best data privacy consultants as well as an in-house team of experts. The first 30 days are about clarity and quick wins. We interview stakeholders, inventory systems, and map data flows. We publish a risk register with prioritized fixes and an executive roadmap that sequences the work. In parallel, we implement a consent solution that fits your footprint and regions, aligning banner text with your notices and wiring consent into the tools that actually send data out of your environment. By day 30 you have updated notices, a working CMP and preference center for at least one major surface, and a DSAR intake channel with identity-safe verification. Days 31 to 90 are about depth and durability. We complete your Record of Processing Activities, align each dataset with a lawful basis, and publish a retention schedule. We build deletion automations in the systems that hold personal data, and we configure dashboards to evidence what was deleted and when. We establish vendor governance with standard DPAs, sub-processor disclosures, deletion SLAs, and a lightweight recertification rhythm. If you rely on ads and analytics in consented regions, we enable standardized signals and server-side gating, and we validate that declines truly shut off processing. We also run a tabletop exercise so lines of communication are proven before you need them. After 90 days, the program moves into operate-and-improve mode. Each quarter we deliver deletion and consent evidence, refresh the vendor registry, review incidents and rights requests, and update training. For growth initiatives, we run change-management: new SDKs, endpoints, or customer data programs are reviewed against your purposes, lawful bases, and retention plan. This rhythm reduces ad hoc approvals and lets teams ship within clear guardrails. Because everything is instrumented, you can report KPIs to leadership: DSAR cycle time, consented audience size and performance, vendor posture, and incidents resolved. The method is simple but uncommon—state what you do, do what you state, and continuously prove it with artifacts generated by the systems themselves.
Core Services and Deliverables: Privacy Ops You Can See and Use
Our software was built to be used in tandem with data privacy consulting services which are built to deliver tangible artifacts your teams can rely on from day one. The Privacy Program Assessment produces an executive dashboard with maturity scores, a 90-day plan with budget ranges, and a sequence of quick wins that reduce risk immediately. Data Inventory and Mapping codifies where personal data enters, flows, and rests, and it generates or updates your Record of Processing Activities so regulators and partners see that you understand your system. The Lawful Basis and Policy Pack aligns each dataset with contract, legal obligation, legitimate interests, or consent and reconciles those choices with your notices and cookie disclosures. Our DPIA practice covers high-risk scenarios such as location tracking, biometric gates, health-adjacent use cases, and AI features that retain prompts or responses; we document mitigations and approvals to keep decisions traceable. DSAR Operations give customers a simple way to ask for access, deletion, or correction while protecting against identity fraud; we reduce friction by verifying without storing new ID images, and we orchestrate redactions across email, cloud drives, CRMs, and data warehouses. Vendor Risk and DPAs turn contracts into living controls: role definitions, purpose limitation, sub-processor transparency, deletion timelines, and audit rights. Data Minimization and Retention Automation stop hoarding: we set short defaults by purpose and create purge jobs that run on a schedule, then produce deletion logs to prove it happened. Incident and Breach Readiness establishes playbooks, contact trees, and templates so the first 72 hours are calm and competent. Finally, AI Governance sets guardrails for model inputs, retention, explainability, and user transparency—especially important in regulated or sensitive domains. The deliverables are not static files; they are connected to dashboards and routines. Each quarter you receive a Deletion and Consent Evidence Report, an updated vendor registry, and a review of incidents and rights requests. This is privacy as operations, which is the only version that scales.
Consent That Performs: TCF v2.2, Consent Mode v2, and Server-Side Enforcement
Consent is only useful if it is both truthful to the user and respected by your tech stack. We implement consent and preference management so a person’s choice is captured clearly and then enforced across the places where data can leak: client-side tags, mobile SDKs, and server-side endpoints. For companies serving or monetizing traffic in the EEA, UK, or Switzerland, we configure standardized signals for partners that expect them, and we integrate gracefully with your analytics, ads, and CDP tooling. When measurement matters, we enable modeling frameworks that respect consent while recovering insight—this might include server-side configuration that forwards only the minimal event set allowed by the person’s choice and region. On mobile, we extend the same pattern so SDK toggles and background events are controlled rather than assumed. Everything is tested with automated scripts that simulate accept, decline, and granular preferences across devices and browsers, and the results are logged so audits are a lookup, not an archeological dig. We also address the human side: consent copy that is plain, consistent with your notice, and honest about trade-offs; a preference center where people can update choices and delete an account without confusion; and customer-support macros that handle common requests with clarity. Because consent now touches growth, we integrate with marketing operations to ensure list building, CRM segmentation, and ad suppression rules match what people have chosen. This is how you turn a banner from a blocker into a performance signal: customers who opt in receive better experiences and more relevant messages, while those who opt out are respected in code. Over time you’ll see healthier metrics—fewer complaints, more durable lists, and better modeled conversions—because your data is earned, not extracted.
Industry Playbooks and Where the ROI Shows Up
No two industries carry the same privacy risk, so our playbooks meet you where you operate. In SaaS and ad-supported media, the work centers on standardized consent signaling, server-side enforcement, and modeling that keeps measurement useful when third-party cookies or mobile identifiers are limited. We help product and growth teams ship experiments inside guardrails so velocity doesn’t stall. In e-commerce and CPG, preference centers and retention discipline are the big wins. We reduce abandoned carts caused by aggressive scripts, align remarketing with actual consent, and trim data bloat so warehouses stay lean. For healthcare-adjacent and financial use cases, we focus on data minimization, role-based access, and strict retention windows allied to security controls, recognizing the heightened sensitivity and contractual obligations. In education and EdTech, we publish transparent AI and data policies for families, restrict model “memory,” and align retention with district or regulator expectations; the payoff is faster procurement and fewer escalations. B2B and professional services benefit from low-PII operations, contract hygiene, and defensible data rooms during sales, diligence, and renewals. Across all sectors, ROI appears in four places: reduced legal and engineering time spent on approvals, lower incident response cost because less data is at risk and evidence is at hand, improved addressability and modeling from consented audiences, and vendor consolidation as redundant tools are retired. To make the value unmistakable, we baseline DSAR cycle time, audience composition, consent rates by placement and copy, and the volume of data purged each quarter. Then we report trends to leadership so privacy’s contribution is visible in the same operating rhythm as revenue and reliability. When teams see privacy reducing toil and unlocking campaigns rather than blocking them, adoption becomes self-reinforcing.
Pricing, Engagement Models, and the Path to Payback
We structure engagements to match your pace and risk profile. Fixed-scope packages give you cost certainty and momentum. A typical Starter program spans six to eight weeks and includes a maturity assessment, updated notices, a live consent and preference center for your primary surface, a DSAR portal with identity-safe verification, and a retention schedule with at least one automated purge job in a system that actually holds personal data. Growth programs extend to vendor governance, server-side enforcement, multi-region consent signaling, and dashboards for deletion and consent evidence; expect twelve to sixteen weeks with meaningful milestones every two to three weeks. Enterprise programs phase in global governance, cross-border transfer controls, and executive reporting that elevates privacy to a board-level metric. If you already have internal operators, we can deliver implementation-only or advisory-only support focused on the hardest parts—consent wiring, retention, or DPIAs for sensitive features. Many clients then move to Fractional DPO or Managed Privacy Ops: a part-time leader plus a steady operational cadence that produces evidence without drama. Payback typically arrives through a combination of labor savings and growth enablement. DSAR automation alone can save dozens of hours per month for teams that previously chased data across email, spreadsheets, and file shares. Vendor consolidation removes duplicative spend. Clean consent signaling stabilizes measurement in constrained regions, which protects revenue. And evidence packs reduce cycles with partners, auditors, and insurers. We encourage clients to treat privacy like reliability: invest in systems and habits that pay back every month through fewer surprises and faster delivery. When you can show deletion volume, consent trends, DSAR cycle time, and incident readiness alongside revenue and uptime, the business case becomes obvious.
Future Privacy Landscape: Requirements You Can’t Ignore
Privacy requirements now come from three directions at once: regulators, platforms, and customers. Regulators continue to tighten expectations on transparency, consent, purpose limitation, and storage limitation, and they expect timely rights responses with identity-safe verification. State laws in the United States keep expanding, adding rules on sensitive categories, ad targeting, health data, and data broker registration. Internationally, enforcement emphasizes whether consent banners are honest and whether opt-outs actually change what your systems do—not simply what your policy says. Platforms have become de-facto rule-makers. In parts of the world, ads and analytics depend on standardized consent signals, and partners expect you to use a certified consent solution and to pass accurate signals for each request. Without that plumbing, growth teams will struggle to measure, optimize, or even run campaigns. Customers, meanwhile, are savvy. They notice whether “reject” works, whether deletion actually deletes, and whether your product remembers more than they expected. They compare your notices to your behavior. They share screenshots and experiences publicly. That is why durable programs are built to be verifiable: consent logs tied to identifiers you can reconcile, deletion evidence generated by the systems that purged the data, and policies that match the product. Looking ahead, two trends stand out. First, AI governance is moving from whitepapers to controls—clear limits on training data, retention, and transparency, especially for education, health, and finance. Second, server-side architectures are becoming standard, which is good for performance and security but dangerous if used to bypass consent. The right approach is to treat server-side like any other processing surface: gated by user choice and purpose, logged, and included in audits. If you align to these realities now, you’ll avoid the scramble each time a platform announces changes or a regulator launches a sweep. Privacy is no longer a quarterly project; it’s an operating discipline like security and reliability.
Buyer FAQs: Straight Answers You Can Use Internally
What does a privacy consultant actually do? A privacy consultant makes your data practices lawful, transparent, and enforceable in code. That means inventorying data, mapping purposes and lawful bases, updating notices, wiring consent and opt-outs through web, app, and server-side, automating retention and deletion, tightening vendor contracts, and producing evidence so you can answer questions from regulators, partners, and customers quickly and credibly.
Do we really need a consent platform if we mostly sell in the U.S.? If you reach or plan to reach consent-constrained regions, yes. Even in the U.S., a proper consent and preference layer is best practice for record-keeping and user trust, and it simplifies suppression rules across channels. There is a ton of litigation happening over CIPA claims and any great privacy consultant will tell you to watch out for lawsuits from Swigart, Tauler Smith, Pacific Trial Attorneys, or the other dozen or so law firms coming after business owners with Meta-Pixel claims. So yes you absolutely should be using a Captain Compliance consent banner on your site.
How long until we’re “good”? Most companies achieve a strong baseline in six to twelve weeks, then move to a steady cadence of operation and improvement with quarterly evidence. This is called maturing the privacy program to achieve your ongoing goals.
How is privacy different from security? Security prevents unauthorized access; privacy governs authorized collection and use. You need both. Security alone won’t give you lawful bases, consent records, deletion evidence, or contract discipline with vendors.
Can you work with our stack? Yes. We integrate with common analytics, ads, tag managers, SDKs, CDPs, warehouses, help desks, and storage systems. We replace tools only when there’s a clear benefit in risk reduction or cost.
What if we already have a banner? We’ll test whether decline truly shuts off client-side, app, and server-side flows. If not, we’ll fix the wiring and give you logs to prove it works.
What if leadership wants ROI? We baseline DSAR cycle time, consent rates, deletion volume, incident readiness, and audience performance. Then we show how those metrics improve quarter over quarter as the program matures. These answers help align legal, security, product, and growth around the same operating picture: privacy as a measurable, repeatable system that reduces risk and increases the value of your data.
Ready to Turn Privacy Into Performance? Recommended Data Privacy Consultants
We have a list of some of the top privacy consultants you can work with. If you let us know your region, industry, and needs we will place you with an expert to help.
Privacy is no longer a perimeter around your business; it is part of how your business works. When you treat it like operations—instrumented, auditable, and continuously improved—you reduce risk, accelerate launches, and build data you can actually use. Captain Compliance brings the playbooks and the platform to get you there in weeks, not quarters. Book a strategy session and we’ll map your first ninety days, show you how consent becomes a performance signal, and set up the evidence cadence that lets you answer tough questions with confidence.