Privacy breaches no longer occupy the margins of corporate risk registers—they dominate boardroom agendas, drive market valuations, and determine competitive positioning. When British Airways faced a £20 million GDPR fine, when Meta accumulated over €2.5 billion in privacy penalties, and when healthcare organizations paid $16.2 million on average for data breach costs in 2024, the message became unmistakable: privacy is not merely a compliance obligation. It is a material enterprise risk demanding the same strategic attention, resource allocation, and governance oversight as financial, operational, and reputational risks.
Yet most organizations still treat privacy as a siloed compliance function, disconnected from enterprise risk management (ERM) frameworks that guide strategic decision-making. This structural disconnect creates blind spots in risk assessments, misallocates resources, and leaves boards without adequate visibility into one of their most significant liability exposures.
This comprehensive guide demonstrates how to integrate privacy into enterprise risk management frameworks, establish board-level governance, quantify privacy risk in financial terms, and transform data protection from a compliance checkbox into a strategic risk discipline that protects enterprise value.
GET A FREE ENTERPRISE PRIVACY AUDIT FROM CAPTAINCOMPLIANCE.COM CLICK HERE
Understanding Privacy as Enterprise Risk
Traditional enterprise risk management categorizes organizational threats across financial, operational, strategic, and compliance dimensions. Privacy risk intersects all four categories, creating compound exposure that amplifies impact and complicates mitigation.
The Multi-Dimensional Nature of Privacy Risk
Financial Risk: Direct monetary exposure from regulatory fines, litigation costs, breach notification expenses, forensic investigations, credit monitoring services, and regulatory audit responses. GDPR fines can reach €20 million or 4% of global annual revenue—whichever is higher. U.S. state privacy laws impose penalties ranging from $2,500 to $7,500 per violation, with some violations calculated per affected individual. Class action litigation adds exposure ranging from millions to billions depending on breach scope and data sensitivity.
Operational Risk: Business disruption from privacy incidents, system shutdowns for forensic analysis, lost productivity during incident response, degraded customer service during breach notification periods, and diverted resources from strategic initiatives to remediation efforts. Healthcare organizations report average operational downtime of 21 days following ransomware attacks affecting patient data—translating to millions in lost revenue and compromised patient care.
Strategic Risk: Market share loss to privacy-conscious competitors, customer attrition following breach disclosure, impaired ability to execute data-driven strategies, restricted market access in jurisdictions with strict privacy requirements, and diminished enterprise valuation. Studies demonstrate that companies experience average stock price declines of 7.27% following breach announcements, with recovery periods extending months or years.
Reputational Risk: Brand damage, erosion of customer trust, negative media coverage, social media backlash, difficulty recruiting talent concerned about employer data practices, and loss of business partnerships with privacy-sensitive organizations. Reputational damage often exceeds direct breach costs IBM’s 2025 Cost of a Data Breach Report identifies lost business as the largest cost component at $1.68 million average per incident and an average of $4.44 million.
Compliance Risk: Regulatory enforcement actions, consent decrees imposing ongoing monitoring requirements, restrictions on data processing activities, mandated implementation of specific controls, and heightened scrutiny for future compliance assessments. Organizations under privacy consent decrees face years of regulatory oversight, independent assessments, and restricted operational flexibility.
Why Privacy Demands ERM Integration
Privacy risks are not static—they evolve with business model changes, technology adoption, regulatory developments, and threat landscape shifts. ERM frameworks provide the structured methodology to continuously assess, prioritize, monitor, and mitigate these dynamic risks across enterprise operations.
Integration delivers tangible benefits: unified risk language enabling board-level discussion, coordinated mitigation strategies addressing root causes rather than symptoms, resource allocation aligned with actual risk exposure rather than compliance budgets, and enterprise-wide ownership replacing siloed privacy team responsibility.
Organizations that successfully integrate privacy into ERM report better board engagement, more effective resource allocation, proactive risk identification, and enhanced ability to demonstrate accountability to regulators, customers, and business partners.
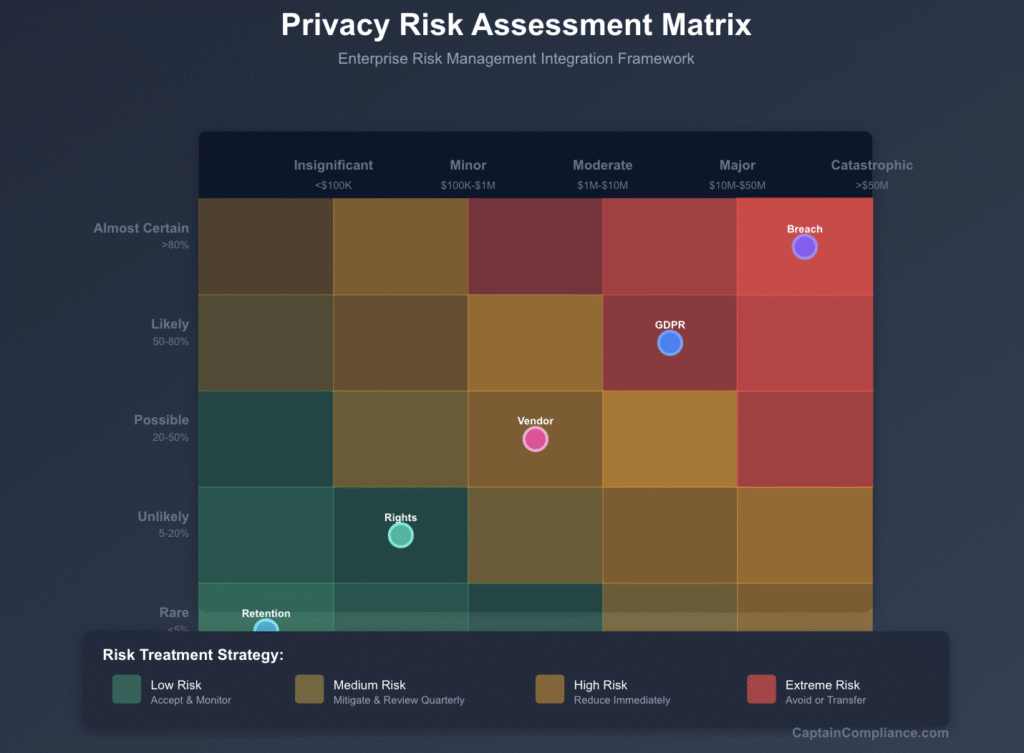
Mapping Privacy Risk to Established ERM Frameworks
Effective integration requires translating privacy-specific risks into the language and methodologies of established enterprise risk management frameworks.
ISO 31000 Risk Management Framework
ISO 31000 provides principles and guidelines for risk management applicable across all risk types. Integrating privacy requires:
Risk Identification: Systematic inventory of privacy risks across data lifecycle—collection, processing, storage, sharing, retention, and deletion. Identify risks at both strategic level (regulatory landscape changes, evolving consumer expectations, competitive positioning) and operational level (vendor data breaches, employee access violations, system vulnerabilities).
Risk Analysis: Evaluate likelihood and consequence of identified privacy risks using established organizational scales. Likelihood assessment considers threat landscape (cybercriminal sophistication, insider threat prevalence, vendor security postures), control effectiveness (technical safeguards, organizational processes, governance mechanisms), and historical incident data. Consequence assessment quantifies potential financial impact, operational disruption, strategic setbacks, and reputational damage using consistent measurement criteria applied to all enterprise risks.
Risk Evaluation: Compare privacy risk levels against organizational risk appetite and tolerance thresholds. Determine which risks require treatment, which are acceptable within tolerance, and which demand escalation to board level. This evaluation should align privacy risk decisions with broader strategic risk decisions—applying consistent criteria whether evaluating privacy risks, cybersecurity risks, or financial risks.
Risk Treatment: Develop mitigation strategies using the four standard approaches: avoid (eliminate high-risk processing activities), reduce (implement controls decreasing likelihood or impact), transfer (leverage cyber insurance, contractual indemnification, or risk-sharing arrangements), or accept (document conscious decision to retain risks within tolerance). Privacy risk treatment plans should integrate with existing control frameworks rather than creating parallel compliance programs.
Monitoring and Review: Establish continuous assessment mechanisms tracking privacy risk evolution. Monitor regulatory developments, emerging threats, control effectiveness metrics, and near-miss incidents. Regular review cycles should align with broader ERM reporting cadences, ensuring privacy risk updates inform strategic decision-making alongside other material risks.
COSO ERM Framework
The Committee of Sponsoring Organizations (COSO) Enterprise Risk Management Framework emphasizes risk management’s role in strategy and performance. Privacy integration requires:
Governance and Culture: Establish board-level oversight of privacy risks through dedicated committee responsibility or integration into existing audit or risk committees. Define organizational privacy risk appetite statements aligned with strategic objectives—e.g., “We will not engage in data processing activities that create >15% probability of material regulatory enforcement within any 12-month period.” Embed privacy accountability into performance management, compensation structures, and cultural expectations.
Strategy and Objective-Setting: Incorporate privacy considerations into strategic planning processes. When evaluating new markets, assess privacy regulatory requirements as market entry criteria. When adopting new technologies (AI, IoT, biometrics), evaluate privacy risks alongside operational benefits. Ensure privacy risk appetite informs strategic risk-taking—avoiding strategies that exceed appetite regardless of potential returns.
Performance: Establish privacy risk key risk indicators (KRIs) integrated into enterprise risk dashboards. Track metrics including: percentage of high-risk processing activities with completed DPIAs, mean time to privacy incident detection and notification, vendor privacy risk scores, privacy training completion rates, and subject rights request fulfillment timelines. These KRIs should trigger escalation when approaching tolerance thresholds, enabling proactive intervention before risk crystallizes.
Review and Revision: Conduct formal privacy risk assessments aligned with broader ERM assessment cycles. Annual strategic reviews should evaluate whether privacy risk appetite remains appropriate given business model evolution, regulatory landscape changes, and threat environment shifts. Incident post-mortems should feed lessons learned into both privacy controls and broader ERM methodology improvements.
Information, Communication, and Reporting: Develop privacy risk reporting mechanisms tailored to audience needs. Board reports should quantify privacy risks in financial terms, compare against risk appetite, and present clear decision points. Executive reports should provide operational detail on mitigation progress, incident trends, and resource requirements. Operational reports should deliver tactical guidance for risk owners implementing controls.
NIST Risk Management Framework
The National Institute of Standards and Technology (NIST) Risk Management Framework provides a process for integrating security and privacy risk management into system development lifecycles. While originally focused on federal systems, NIST RMF principles apply broadly:
Categorize: Classify information systems based on privacy impact levels. Systems processing sensitive personal data (health information, financial records, biometric data, children’s data) receive high-impact categorization triggering enhanced security and privacy controls. Systems processing basic contact information receive lower categorization with proportionate controls.
Select: Choose privacy control baselines from NIST Special Publication 800-53 aligned with system categorization. Controls span authority and purpose (documenting legal basis for processing), accountability and audit (establishing responsibility and logging), data quality and integrity (ensuring accuracy), data minimization (limiting collection and retention), individual participation (enabling subject rights), security (protecting confidentiality and integrity), transparency (providing notice), and use limitation (enforcing purpose restrictions).
Implement: Deploy selected privacy controls within system architectures and operational processes. Implementation should integrate privacy controls with security controls—avoiding duplicative efforts while ensuring comprehensive protection. Document control implementation in system security and privacy plans.
Assess: Evaluate control effectiveness through testing, inspection, and interviews. Assessment should validate that controls operate as designed and achieve intended privacy outcomes. Independent assessment provides objectivity and credibility with both internal stakeholders and external regulators.
Authorize: Senior leadership accepts residual privacy risks following control implementation and assessment. Authorization represents explicit acknowledgment of remaining risks and conscious decision that these risks fall within organizational tolerance. This authorization should align with broader risk acceptance frameworks applied to other enterprise risks.
Monitor: Continuously track control effectiveness, emerging threats, regulatory changes, and system modifications that may alter privacy risk profile. Monitoring should feed into broader continuous monitoring programs providing enterprise-wide risk visibility.
GDPR and Privacy-Specific Frameworks
While ERM frameworks provide structure, GDPR and privacy-specific frameworks define substantive requirements:
GDPR Risk-Based Approach: GDPR Articles 24 and 25 require controllers to implement “appropriate technical and organizational measures” considering processing risks to individual rights and freedoms. Data Protection Impact Assessments (DPIAs) under Article 35 mandate formal risk assessment for high-risk processing. These GDPR requirements should integrate directly into ERM risk assessment processes—not exist as parallel compliance exercises.
Privacy Risk Assessment Frameworks: Frameworks like ISO/IEC 29134 (Privacy Impact Assessment) and NIST Privacy Framework provide structured methodologies for privacy risk assessment. These specialized frameworks offer granular privacy risk taxonomies and assessment criteria that should inform—but not replace—enterprise-level risk evaluation using organizational risk scales and appetite statements.
Privacy Management Accountability Frameworks: ISO/IEC 27701 (Privacy Information Management) and AICPA SOC 2 criteria provide frameworks for privacy program governance, control implementation, and accountability demonstration. These frameworks establish operational expectations that translate privacy strategy into daily practice.
Quantifying Privacy Risk in Financial Terms
Board-level risk discussions require financial quantification. Privacy risk must be expressed in monetary terms comparable to other enterprise risks to enable informed resource allocation and risk acceptance decisions.
Direct Cost Components
Regulatory Penalties: Calculate potential exposure using regulatory maximums applied to organizational circumstances. For GDPR, assess both the €20 million cap and the 4% global revenue threshold—applying whichever is higher. For CCPA and state privacy laws, multiply potential violations by per-violation penalties, considering whether violations are calculated per incident or per affected individual based on jurisdictional interpretation.
Litigation Costs: Model class action exposure using industry precedent. Healthcare data breaches average $100-$300 per record in settlement costs. Financial data breaches average $250-$500 per record. Biometric data litigation settlements have reached $650 per affected individual. Legal defense costs average $2-5 million regardless of case outcome.
Breach Response Costs: Quantify incident response expenses including forensic investigation ($50,000-$500,000 depending on scope), notification costs ($5-$15 per affected individual including mail, call center, and legal review), credit monitoring services ($15-$25 per individual per year for 1-3 years), and public relations response ($100,000-$1,000,000 for significant incidents).
Remediation Investments: Calculate costs for implementing enhanced controls following incidents or regulatory orders, including technology purchases, consulting engagements, staff augmentation, and process redesign. Post-incident remediation averages 3-5x the cost of proactive implementation.
Indirect Cost Components
Lost Business: Model customer attrition using industry research. Studies show 60-75% of consumers would switch providers following a breach affecting their personal data. Calculate revenue impact across multi-year customer lifetime value, not just immediate churn.
Operational Disruption: Quantify productivity losses during incident response, system downtime costs, diverted resources from strategic projects, and delayed product launches. Healthcare organizations report $100,000-$300,000 daily revenue loss during ransomware-related operational disruption.
Market Valuation Impact: Apply historical stock price decline percentages (average 7.27% following breach disclosure) to current market capitalization. While actual impact varies, this provides board-comprehensible scale of potential shareholder value destruction.
Insurance Premium Increases: Model cyber insurance cost increases following incidents. Organizations experiencing breaches see average premium increases of 20-50% at next renewal, with some facing non-renewal requiring more expensive alternative coverage.
Strategic Opportunity Costs: Quantify lost opportunities from customers requiring privacy certifications you lack, markets you cannot enter due to privacy risks, partnerships rejected due to data protection concerns, and innovations you cannot pursue due to privacy constraints.
Risk Quantification Methodologies
Factor Analysis of Information Risk (FAIR): FAIR provides structured quantitative risk analysis expressing risk in financial terms. The model separates loss event frequency (how often privacy incidents occur) from loss magnitude (impact when they occur), using probability distributions to model uncertainty. FAIR analysis produces annual loss expectancy figures directly comparable to other financial risk metrics.
Monte Carlo Simulation: Use Monte Carlo methods to model privacy risk scenarios accounting for probability distributions in both likelihood and impact variables. Simulation produces risk ranges (e.g., 90% confidence that annual privacy losses will fall between $2M-$8M) rather than single-point estimates, better reflecting inherent uncertainty in risk assessment.
Scenario Analysis: Develop detailed breach scenarios reflecting realistic threat profiles (ransomware attack encrypting customer databases, third-party vendor breach exposing shared data, insider theft of sensitive records, misconfigured cloud storage publicly exposing proprietary data). Quantify each scenario’s financial impact and assess probability, producing expected annual loss figures for each scenario and aggregate portfolio risk.
Benchmarking: Compare privacy risk exposure and mitigation spending against industry peers using benchmarking data from sources like IBM Cost of a Data Breach Report, Ponemon Institute studies, and Privacy Analytics research. Benchmarking provides validation that risk quantification reflects realistic scenarios and that mitigation investments align with industry norms.
Establishing Board-Level Privacy Risk Governance
Effective privacy risk management requires board engagement beyond perfunctory compliance updates. Boards must exercise active oversight, receive risk-relevant reporting, and make informed strategic decisions incorporating privacy considerations.
Board Committee Structure
Privacy Oversight Assignment: Designate specific board committee responsibility for privacy risk oversight. Options include:
- Audit Committee: Leverages existing risk oversight mandate, financial expertise, and regulatory compliance focus. Works well when privacy risks primarily manifest as financial and compliance exposures.
- Risk Committee: Provides natural home for privacy as enterprise risk, enables integration with other strategic risks, and positions privacy alongside cybersecurity oversight. Optimal for organizations with mature ERM programs.
- Technology Committee: Appropriate when privacy risks closely couple with technology decisions around cloud adoption, AI deployment, or digital transformation initiatives.
- Dedicated Privacy Committee: Justifiable for organizations where data is core business asset (adtech, healthtech, fintech) and privacy risk exposure is material to enterprise valuation.
Regardless of assignment, committee charters should explicitly include privacy risk oversight responsibilities, define reporting cadence, specify escalation thresholds, and establish expertise expectations for committee members.
Board Reporting Framework
Quarterly Privacy Risk Dashboard: Provide concise executive summary presenting:
- Risk Heatmap: Visual representation of privacy risk portfolio showing risk distribution across likelihood/impact matrix, highlighting movement from prior period
- Key Risk Indicators: Trend data on leading indicators including incident detection time, vendor risk scores, control effectiveness ratings, and near-miss frequency
- Risk Appetite Compliance: Status against established appetite statements, flagging any metrics approaching or exceeding tolerance thresholds
- Material Risk Changes: Narrative describing significant changes in risk profile from regulatory developments, business model evolution, or threat landscape shifts
- Mitigation Progress: Status of in-flight risk treatment initiatives, highlighting completed milestones and identifying obstacles requiring board attention
- Financial Exposure: Quantified annual loss expectancy using methodologies described above, trended over time and compared against mitigation spending
Annual Privacy Risk Strategy: Comprehensive review covering:
- Risk Landscape Assessment: Analysis of regulatory environment, emerging threats, competitive positioning, and stakeholder expectations
- Risk Appetite Review: Evaluation of whether current appetite statements remain appropriate given strategic direction and market conditions
- Privacy Program Maturity: Assessment against industry frameworks (ISO 27701, NIST Privacy Framework) with gap analysis and roadmap
- Investment Recommendations: Business case for privacy risk mitigation investments, including ROI analysis comparing mitigation costs against expected risk reduction
- Strategic Risk Considerations: Privacy implications of planned strategic initiatives (M&A, new market entry, technology adoption, business model evolution)
Incident Reporting: Immediate notification protocols for material privacy incidents requiring board awareness. Define materiality thresholds (e.g., affecting >10,000 individuals, involving sensitive data categories, triggering regulatory notification, creating significant media attention) and establish 24-48 hour reporting timelines ensuring board notification before public disclosure when possible.
Board Privacy Competency Development
Effective oversight requires board member privacy literacy. Organizations should provide:
Onboarding Education: New board members receive privacy fundamentals covering applicable regulations, organizational privacy risk profile, governance structure, and recent incident history. Education should be tailored to member expertise—deeper technical detail for technology-savvy members, strategic focus for business operations experts.
Continuing Education: Annual updates on privacy landscape evolution, emerging technologies creating new risks, regulatory developments, and evolving best practices. Utilize external experts providing independent perspective on organizational privacy posture.
Tabletop Exercises: Facilitated breach scenario simulations engaging board in crisis decision-making, testing escalation protocols, and exposing gaps in governance structures. Exercises should create realistic pressure testing judgment under time constraints and incomplete information.
Integrating Privacy Risk Into Existing ERM Programs
Successful integration requires methodical approach embedding privacy into established risk management processes rather than creating parallel structures.
Phase 1: Risk Inventory and Mapping
Privacy Risk Taxonomy Development: Create privacy-specific risk categories aligned with organizational risk taxonomy. Categories should include:
- Unauthorized access and disclosure risks (external breaches, insider threats, accidental exposure)
- Regulatory compliance risks (GDPR violations, state law non-compliance, sector-specific regulation breaches)
- Processing legitimacy risks (lack of valid legal basis, purpose limitation violations, excessive retention)
- Individual rights risks (subject access request failures, deletion request non-compliance, rights exercised in bad faith creating operational burden)
- Vendor and third-party risks (processor breaches, subprocessor violations, inadequate due diligence)
- Technology and innovation risks (AI bias and discrimination, IoT device vulnerabilities, emerging technology unknowns)
Risk Owner Assignment: Designate risk owners from business units and functional areas accountable for managing specific privacy risks. Ownership should align with existing ERM risk ownership structure—leveraging established accountability rather than creating privacy-specific parallel. For example, the Chief Technology Officer owns technology infrastructure privacy risks, the Chief Human Resources Officer owns employee data privacy risks, and business unit leaders own customer data privacy risks within their domains.
Risk Register Integration: Incorporate privacy risks into enterprise risk register using consistent formatting, assessment criteria, and treatment planning as other risks. Privacy risks should not occupy separate privacy-specific register—integration signals that privacy risks receive equivalent treatment and visibility as operational, financial, and strategic risks.
Phase 2: Assessment Methodology Alignment
Unified Risk Scales: Assess privacy risks using organizational likelihood and impact scales applied to all enterprise risks. Avoid creating privacy-specific scales that complicate comparison and resource allocation across risk types. If organizational scales use 1-5 likelihood ratings (rare, unlikely, possible, likely, almost certain) and 1-5 impact ratings (insignificant, minor, moderate, major, catastrophic), apply these same scales to privacy risks.
Impact Calibration: Calibrate privacy risk impact ratings to organizational impact definitions. If “major” impact is defined as $10M-$50M financial exposure, then privacy risks with that financial exposure receive “major” ratings—ensuring consistent treatment whether evaluating privacy breach costs, foreign exchange risks, or supply chain disruptions.
Risk Appetite Incorporation: Privacy risks should be evaluated against organizational risk appetite statements. If risk appetite states “We will not accept risks with >20% likelihood of major impact without board approval,” this applies equally to privacy risks. Privacy-specific appetite statements should augment, not replace, organizational appetite—adding nuance about acceptable data processing practices while maintaining consistency with broader risk tolerance.
Phase 3: Treatment and Mitigation Integration
Control Framework Harmonization: Map privacy controls to existing control frameworks (COSO Internal Control, SOC 2, ISO 27001) rather than treating privacy controls as entirely distinct. Many privacy controls leverage existing security and operational controls—access management, encryption, change management, vendor management. Avoid duplicative controls by establishing control mappings showing how existing controls satisfy multiple requirements.
Capital Allocation Process: Privacy risk mitigation investments should flow through established capital allocation processes competing alongside other risk mitigation investments and strategic initiatives. Privacy should not operate from separate budget unconnected to organizational priorities—instead, privacy leaders should justify investments using same business case requirements applied to cybersecurity, operational efficiency, or business continuity investments.
Mitigation Tracking: Monitor privacy risk treatment progress using program management tools and methodologies applied to other enterprise initiatives. Privacy mitigation projects should follow established project governance, reporting into PMO structures, and adhering to stage-gate approval processes ensuring appropriate oversight and resource management.
Phase 4: Monitoring and Reporting Integration
KRI Dashboard Consolidation: Incorporate privacy key risk indicators into enterprise risk dashboards providing unified view of organizational risk posture. Executives and board members should see privacy metrics alongside cybersecurity, financial, operational, and strategic risk indicators—enabling holistic understanding of risk portfolio.
Reporting Cadence Alignment: Privacy risk reporting should follow established ERM reporting rhythms. If enterprise risks are reviewed monthly at executive risk committee, quarterly at board level, and annually for strategic assessment, privacy risks should follow identical cadence—not exist on separate reporting schedules creating fragmentation and information gaps.
Risk Committee Participation: Privacy leaders should participate in established risk committee meetings as subject matter experts—similar to how cybersecurity, finance, and operations leaders present their risk domains. This participation signals organizational commitment to integrated risk management and ensures privacy perspectives inform cross-functional risk discussions.
Third-Party and Vendor Privacy Risk Management
Third-party relationships create extended privacy risk exposure requiring rigorous vendor risk management integrated with broader third-party oversight programs.
Vendor Risk Assessment Framework
Initial Due Diligence: Comprehensive privacy assessment before engaging vendors processing personal data. Assessment should evaluate:
- Data Processing Scope: What personal data categories will vendor access? What processing activities will they perform? Where will data be stored and processed geographically?
- Security Controls: What technical safeguards protect personal data? Do controls meet organizational standards and regulatory requirements?
- Privacy Governance: Does vendor have documented privacy program? Is there designated privacy leadership? What privacy training do personnel receive?
- Compliance Posture: What privacy certifications does vendor hold (ISO 27701, SOC 2 Type II, HIPAA attestation)? Have they experienced breaches or regulatory enforcement?
- Contractual Protections: Will vendor accept data processing agreement meeting GDPR Article 28 requirements? Will they provide adequate security, breach notification, audit rights, and data return/destruction commitments?
- Financial Viability: Is vendor financially stable? Could bankruptcy or acquisition create privacy risks from control lapses or asset transfers?
Risk Scoring Methodology: Assign vendor privacy risk scores based on assessment findings, data sensitivity, processing scope, and vendor security posture. Risk scores should align with organizational vendor risk rating scales, enabling consistent treatment of privacy risks alongside cybersecurity, financial, and operational vendor risks.
Risk-Based Approach: Differentiate vendor oversight based on risk scores. High-risk vendors (processing sensitive personal data, performing critical functions, demonstrating control deficiencies) receive enhanced scrutiny including onsite audits, continuous monitoring, and frequent reassessment. Lower-risk vendors (processing limited data, strong controls, mature privacy programs) receive lighter-touch monitoring.
Ongoing Vendor Monitoring
Continuous Assessment: Implement ongoing monitoring detecting vendor privacy risk changes. Monitor for:
- Breach Notifications: Vendor security incidents potentially affecting shared personal data
- Certification Lapses: Expiration of SOC 2 reports, ISO certifications, or privacy attestations without renewal
- Regulatory Actions: Enforcement actions against vendor creating heightened risk
- Financial Distress: Bankruptcy, layoffs, or acquisition activities creating control risk
- Control Changes: Vendor infrastructure migrations, subprocessor additions, or security changes altering risk profile
Periodic Reassessment: Conduct formal vendor privacy reassessments on risk-based schedules (annually for high-risk vendors, every 2-3 years for lower-risk vendors). Reassessment validates that initial due diligence findings remain accurate and controls remain effective.
Audit Rights Exercise: Contractual audit rights should be exercised periodically, particularly for high-risk vendors. Audits validate control effectiveness, identify emerging risks, and demonstrate accountability to regulators that due diligence extends beyond initial assessment to ongoing verification.
Vendor Incident Response Integration
Notification Requirements: Contracts should mandate vendor notification within defined timeframes (typically 24-48 hours) when incidents affect shared personal data. Notification should include sufficient detail enabling assessment of regulatory notification obligations and customer communication requirements.
Coordinated Response: Incident response plans should address vendor-originated incidents including escalation protocols, forensic support expectations, and communication coordination. Organizations remain accountable to regulators and customers even when vendors cause breaches—requiring tight coordination ensuring rapid response and consistent messaging.
Post-Incident Assessment: Following vendor incidents, conduct root cause analysis informing vendor risk reassessment. Significant incidents may trigger enhanced monitoring, additional contractual protections, or vendor replacement if risks exceed tolerance.
Privacy Risk Culture and Organizational Change
Technical controls and governance structures fail without organizational culture recognizing privacy risk significance and supporting risk-conscious behavior.
Executive Leadership Alignment
C-Suite Privacy Advocacy: Chief Executive Officers must articulate privacy as enterprise priority—not merely DPO concern. CEO communication should position privacy as competitive differentiator, customer expectation, and risk management imperative deserving investment and attention alongside other strategic priorities.
Cross-Functional Ownership: Privacy risk management requires collaboration across legal, technology, security, operations, marketing, and business units. Executive leaders must break down silos by establishing cross-functional privacy councils, joint objectives, and shared accountability metrics.
Resource Commitment: Leadership must allocate sufficient resources—budget, personnel, and time—enabling effective privacy risk management. Under-resourced privacy programs cannot deliver on ambitious governance commitments, creating false sense of control while risks remain inadequately addressed.
Employee Awareness and Training
Role-Based Training: Privacy training should be differentiated by employee role and data access. Executives receive strategic privacy risk training covering board governance, risk quantification, and strategic implications. Developers receive privacy-by-design and secure coding training. Marketing personnel receive consent management and purpose limitation training. Customer service representatives receive data minimization and access control training.
Scenario-Based Learning: Move beyond compliance checkbox training to engaging scenario-based learning testing judgment in realistic situations. Scenarios should present ambiguous situations requiring risk-benefit analysis—building organizational capacity for privacy-conscious decision-making in gray areas where policies provide incomplete guidance.
Continuous Reinforcement: Annual compliance training is insufficient. Privacy awareness requires continuous reinforcement through newsletters, phishing simulations testing privacy awareness, lunch-and-learn sessions, and integration into team meetings ensuring privacy remains top-of-mind rather than once-yearly obligation.
Incentive Alignment
Performance Management Integration: Privacy risk management metrics should factor into performance reviews for relevant roles. Security teams measured on incident prevention and response. Product teams measured on privacy-by-design adoption. Customer service teams measured on subject rights request handling. When compensation and advancement depend partly on privacy outcomes, behavior changes follow.
Positive Recognition: Recognize and reward privacy-conscious behavior publicly. Celebrate teams that proactively identify privacy risks, implement innovative privacy-enhancing technologies, or demonstrate exceptional incident response. Positive recognition creates cultural norms where privacy risk management is valued and respected.
Accountability for Failures: Establish clear consequences for privacy policy violations or reckless behavior creating privacy risks. Accountability need not be punitive—often coaching and remedial training suffice for good-faith errors. However, repeated violations or intentional disregard for privacy requirements demand progressive discipline ensuring organizational norms are maintained.
Measuring Privacy Risk Management Maturity
Organizations at different maturity stages require different risk management approaches. Maturity models provide frameworks assessing current state and roadmaps toward target maturity.
Privacy Risk Maturity Model
Level 1 – Initial: Privacy risk management is ad hoc and reactive. No formal privacy risk assessment processes. Incident-driven attention to privacy. Privacy responsibilities unclear. Risk management disconnected from broader ERM.
Level 2 – Developing: Basic privacy risk assessment processes exist but are not consistently applied. Privacy risks documented in some form but not integrated into enterprise risk register. Privacy resources allocated but often insufficient. Privacy considered primarily compliance function.
Level 3 – Defined: Formal privacy risk assessment methodology aligned with ERM frameworks. Privacy risks integrated into enterprise risk register. Clear ownership and accountability. Risk-based approach to control implementation. Regular privacy risk reporting to executives.
Level 4 – Managed: Quantitative privacy risk assessment producing financial exposure estimates. Board-level privacy risk governance with defined appetite statements. Privacy risks actively monitored with KRIs triggering proactive intervention. Privacy risk culture with accountability embedded in performance management.
Level 5 – Optimized: Privacy risk management fully integrated with ERM producing unified enterprise risk view. Continuous privacy risk monitoring with automated detection and response. Privacy risk intelligence informing strategic decisions. Organization recognized as privacy risk management leader influencing industry standards.
Maturity Assessment and Progression
Organizations should conduct periodic maturity assessments (annually or biannually) evaluating current state across maturity dimensions including governance, risk assessment, quantification, integration, monitoring, culture, and vendor management. Assessment results inform prioritized roadmaps advancing maturity toward target levels.
Progression from Level 1-2 to Level 3 typically requires 12-24 months focusing on establishing foundational processes, integrating with ERM, and building initial capabilities. Advancement from Level 3 to Level 4-5 requires 2-4 years building sophisticated quantification capabilities, embedding privacy risk culture, and achieving sustained operational excellence.
Privacy Risk Management in Mergers and Acquisitions
Mergers, acquisitions, and divestitures create heightened privacy risk requiring specialized risk management approaches integrated with broader M&A due diligence and integration processes.
Pre-Acquisition Privacy Due Diligence
Privacy Risk Assessment: Comprehensive evaluation of target company privacy posture including:
- Regulatory compliance status across all operating jurisdictions
- Historical privacy incidents, breaches, and regulatory enforcement
- Data inventory and classification
- Privacy program maturity and governance structures
- Data processing agreements and vendor relationships
- Pending litigation or regulatory investigations
- Privacy-related contractual commitments to customers
Due diligence should identify material privacy risks creating potential liabilities, integration complexities, or deal value implications. Findings inform valuation adjustments, representations and warranties negotiation, and post-acquisition integration planning.
Deal Structure Considerations
Indemnification and Representations: Negotiate privacy-specific indemnification covering undisclosed breaches, compliance violations, and regulatory actions. Representations and warranties should address compliance status, absence of material incidents, and existence of required consents for data transfers.
Escrow and Holdbacks: Consider escrow arrangements or purchase price holdbacks covering potential privacy liabilities emerging post-closing. GDPR enforcement timelines can extend years after initial violations—requiring extended tail coverage beyond standard 12-18 month survival periods.
Regulatory Approvals: Significant acquisitions may require privacy regulatory approval or notification in certain jurisdictions. GDPR requires notification to data protection authorities when controller identity changes. Some transactions trigger mandatory consultation with works councils regarding employee data processing changes.
Post-Acquisition Integration
Privacy Program Harmonization: Develop integration plan aligning acquired company privacy practices with organizational standards. Prioritize critical gaps creating immediate regulatory risk while allowing phased approach to comprehensive integration over 12-24 months.
Data Integration and Transfer: Plan data consolidation carefully considering transfer restrictions, consent requirements, and retention obligations. GDPR requires legal basis for data transfers between entities. Customers may need notification or re-consent when data controllers change.
Vendor Relationship Management: Review acquired company vendor relationships for privacy compliance, duplicative arrangements, and integration opportunities. Terminate or renegotiate agreements lacking adequate data processing protections.
The Strategic Value of Proactive Privacy Risk Management
Organizations embracing privacy as enterprise risk rather than compliance burden unlock strategic value inaccessible to reactive competitors.
Competitive Differentiation: Privacy-conscious consumers increasingly select providers based on data protection practices. Organizations demonstrating mature privacy risk management win business from privacy-sensitive customers, particularly in healthcare, financial services, and technology sectors where data is core to service delivery.
Market Access: Strong privacy programs enable expansion into privacy-regulated markets. GDPR compliance requirements can create barriers to European market entry. California CPRA, Virginia CDPA, and other state laws similarly gate U.S. market access. Proactive privacy risk management removes these barriers.
Operational Efficiency: Integrated privacy risk management reduces duplicative efforts. When privacy teams work within ERM frameworks rather than parallel compliance structures, organizations avoid redundant assessments, duplicative controls, and conflicting requirements—streamlining operations while improving outcomes.
Innovation Enablement: Clear privacy risk frameworks enable responsible innovation. When organizations understand privacy risk appetite, assessment methodologies, and treatment requirements, product teams can innovate confidently—knowing that privacy risks will be identified, evaluated, and appropriately addressed rather than becoming innovation barriers.
Stakeholder Trust: Customers, employees, business partners, investors, and regulators increasingly evaluate organizations based on privacy practices. Mature privacy risk management builds trust that translates to customer loyalty, talent attraction, favorable partnership terms, lower cost of capital, and regulatory relationships characterized by cooperation rather than adversarial enforcement.
Financial Performance: Research demonstrates correlation between privacy maturity and financial performance. Organizations with strong privacy programs experience fewer costly incidents, lower regulatory penalties, reduced litigation expenses, and higher customer lifetime value. The business case for privacy risk management extends beyond cost avoidance to revenue protection and growth enablement.
Implementation Roadmap: From Compliance to Strategic Risk Management
Organizations transitioning from compliance-focused privacy to integrated enterprise risk management should follow structured implementation approach:
Phase 1: Foundation (Months 1-3)
Stakeholder Alignment: Secure executive and board commitment to privacy risk management elevation. Present business case quantifying current privacy risk exposure, benchmarking organizational maturity, and demonstrating strategic value of integrated approach.
Current State Assessment: Evaluate existing privacy program against enterprise risk management framework integration requirements. Document gaps in governance, assessment methodology, quantification capabilities, reporting mechanisms, and cultural maturity.
Quick Wins Identification: Identify high-impact, low-effort improvements demonstrating early value. Quick wins might include integrating privacy into existing risk register, establishing executive privacy risk dashboard, or quantifying financial exposure for top privacy risks.
Governance Structure Design: Define board oversight responsibilities, committee assignments, reporting cadence, and escalation thresholds. Update committee charters reflecting privacy risk oversight responsibilities.
Phase 2: Integration (Months 4-9)
Risk Inventory and Taxonomy: Complete comprehensive privacy risk identification and develop organizational privacy risk taxonomy aligned with enterprise risk categories. Map privacy risks to business processes, systems, and data flows.
Assessment Methodology Alignment: Align privacy risk assessment with organizational likelihood and impact scales. Calibrate privacy risk impact ratings to organizational impact definitions ensuring consistent treatment across risk types.
Risk Quantification Development: Implement financial quantification methodology (FAIR, Monte Carlo, scenario analysis) producing annual loss expectancy figures for material privacy risks. Begin tracking quantified risk exposure quarterly.
Control Framework Integration: Map privacy controls to existing control frameworks identifying opportunities for consolidation and efficiency. Eliminate duplicative privacy-specific controls leveraging existing security and operational controls where sufficient.
Vendor Risk Integration: Incorporate privacy considerations into vendor risk assessment processes. Ensure vendor privacy due diligence, scoring, monitoring, and incident response integrate with broader third-party risk management.
Phase 3: Operationalization (Months 10-18)
Board Reporting Implementation: Deliver first comprehensive privacy risk board report including risk heatmap, KRI dashboard, risk appetite compliance status, financial exposure quantification, and mitigation recommendations.
Privacy Risk Appetite: Develop and gain board approval for formal privacy risk appetite statements aligned with organizational risk tolerance and strategic objectives.
KRI Dashboard Deployment: Implement privacy key risk indicator monitoring with automated data collection, trend analysis, and threshold alerting. Integrate privacy KRIs into enterprise risk dashboards.
Training and Culture: Launch role-based privacy risk training program, scenario-based learning, and continuous awareness initiatives. Integrate privacy metrics into performance management for relevant roles.
Continuous Monitoring: Establish automated privacy risk monitoring detecting control effectiveness changes, emerging threats, regulatory developments, and vendor risk shifts.
Phase 4: Optimization (Months 19-24)
Maturity Assessment: Conduct formal privacy risk management maturity assessment identifying gaps between current and target state. Develop prioritized roadmap for continued advancement.
Advanced Analytics: Implement predictive analytics identifying leading indicators of privacy risk materialization. Develop machine learning models detecting anomalous data access patterns, privacy policy violations, or vendor risk signals.
Strategic Integration: Embed privacy risk considerations into strategic planning processes, M&A due diligence, product development, and market expansion decisions. Ensure privacy risk appetite informs strategic risk-taking.
Industry Leadership: Contribute to industry privacy risk management standards development. Participate in peer forums sharing lessons learned and advancing collective privacy risk management maturity.
Moving Forward with Strategic Privacy Risk Management
Privacy has evolved from compliance obligation to material enterprise risk demanding board attention, strategic resource allocation, and integrated risk management. Organizations continuing to treat privacy as siloed compliance function will face escalating regulatory exposure, competitive disadvantage, and stakeholder trust erosion as privacy-mature competitors pull ahead.
The pathway forward requires executive commitment, structured implementation, and organizational culture change—but the strategic value justifies the investment. Privacy risk management maturity delivers competitive differentiation, market access, operational efficiency, innovation enablement, stakeholder trust, and financial performance improvements that compound over time.
The frameworks, methodologies, and roadmaps presented in this guide provide actionable foundation for elevating privacy from compliance checkbox to strategic enterprise risk discipline. Organizations implementing these approaches position themselves not merely for regulatory survival but for competitive advantage in privacy-conscious markets where data protection excellence creates tangible business value.
The question is no longer whether privacy merits enterprise risk management integration—the question is whether your organization will lead or lag in making that transition. The organizations answering that question with decisive action today will define competitive standards tomorrow, while those hesitating will find themselves perpetually playing catch-up in an increasingly privacy-regulated, privacy-conscious business environment.
Privacy risk is enterprise risk. The time for integration is now and Captain Compliance is the company to help large enterprises out. Book a demo below with one of our privacy experts below.