Below is the G7 CYBER EXPERT GROUP STATEMENT ON Advancing a Coordinated Roadmap for the Transition to Post-Quantum
Cryptography in the Financial Sector
Why the Financial Sector Is Preparing for the Quantum Era
The G7 Cyber Expert Group advises G7 finance ministers and central bank governors on cyber risks that could threaten the stability of the global financial system. One of the most consequential emerging risks is the advent of cryptographically relevant quantum computing.
While quantum technologies promise breakthroughs in modeling, optimization, and financial analytics, they also pose a fundamental challenge to today’s cryptographic foundations. Sufficiently advanced quantum computers could undermine widely used public-key encryption methods that protect payment systems, financial messaging, identity infrastructure, and sensitive data.
In response, the G7 Cyber Expert Group has articulated a high-level roadmap designed to support a coordinated transition to post-quantum cryptography (PQC) across the financial ecosystem. This roadmap does not establish regulatory mandates or supervisory deadlines. Instead, it provides strategic context, practical considerations, and a shared planning framework intended to help institutions migrate safely, consistently, and in advance of material risk.
Quantum Computing: Opportunity and Systemic Risk
In late 2024, the G7 Cyber Expert Group outlined both the promise and the peril of quantum computing. On the positive side, quantum systems may eventually enable faster portfolio optimization, advanced risk modeling, and new classes of financial products. On the defensive side, however, quantum computers capable of executing large-scale cryptographic attacks could render current public-key algorithms obsolete.
This risk is not uniform across all cryptographic methods. Symmetric encryption is generally more resilient, while public-key cryptography—used for key exchange, digital signatures, authentication, and secure communications—is particularly exposed. The primary mitigation strategy is a transition to quantum-resistant algorithms, many of which already exist and can be deployed on classical infrastructure.
Over the past year, governments, standards bodies, and some financial institutions have begun issuing guidance, developing migration strategies, and piloting quantum-safe solutions. However, cryptographic transition at scale is complex, operationally intensive, and deeply intertwined with third-party technology dependencies—making coordination essential.
Why a Shared Roadmap Matters
Building on earlier work, the G7 Cyber Expert Group developed this roadmap to help senior leaders understand what types of activities may be required, when they may need to occur, and how they can be aligned across jurisdictions.
The roadmap emphasizes preparation rather than reaction. Its purpose is to help organizations move before cryptographic failure becomes a systemic event, preserving operational continuity and financial stability. Timelines are illustrative rather than prescriptive, recognizing that institutions vary widely in size, complexity, and risk exposure.
The roadmap was developed through a dedicated task force comprising financial authorities and industry experts across G7 jurisdictions, informed by extensive consultation with international stakeholders, including National Institute of Standards and Technology, sector-specific information-sharing organizations, and national cybersecurity agencies.
Core Principles Guiding the Transition
The G7 approach to post-quantum migration is anchored in several foundational principles:
Flexibility
Institutions must retain the ability to adapt their plans as technology, standards, and threat intelligence evolve. Continuous monitoring and recalibration are essential features—not afterthoughts.
Risk-Based Prioritization
Not all systems carry equal importance. Organizations may accelerate migration for mission-critical functions while adopting longer timelines for lower-risk applications. Non-critical systems can serve as early pilots to build operational experience.
Standards Alignment
Leveraging established security and service-delivery frameworks—such as ISO-aligned information security management systems—can help institutions measure progress, demonstrate accountability, and coordinate across the ecosystem using shared metrics.
Collaboration Across the Ecosystem
Fragmented approaches increase systemic risk. Cross-border coordination, peer learning, and active engagement with vendors and service providers are essential, particularly for smaller institutions that rely heavily on third-party platforms.
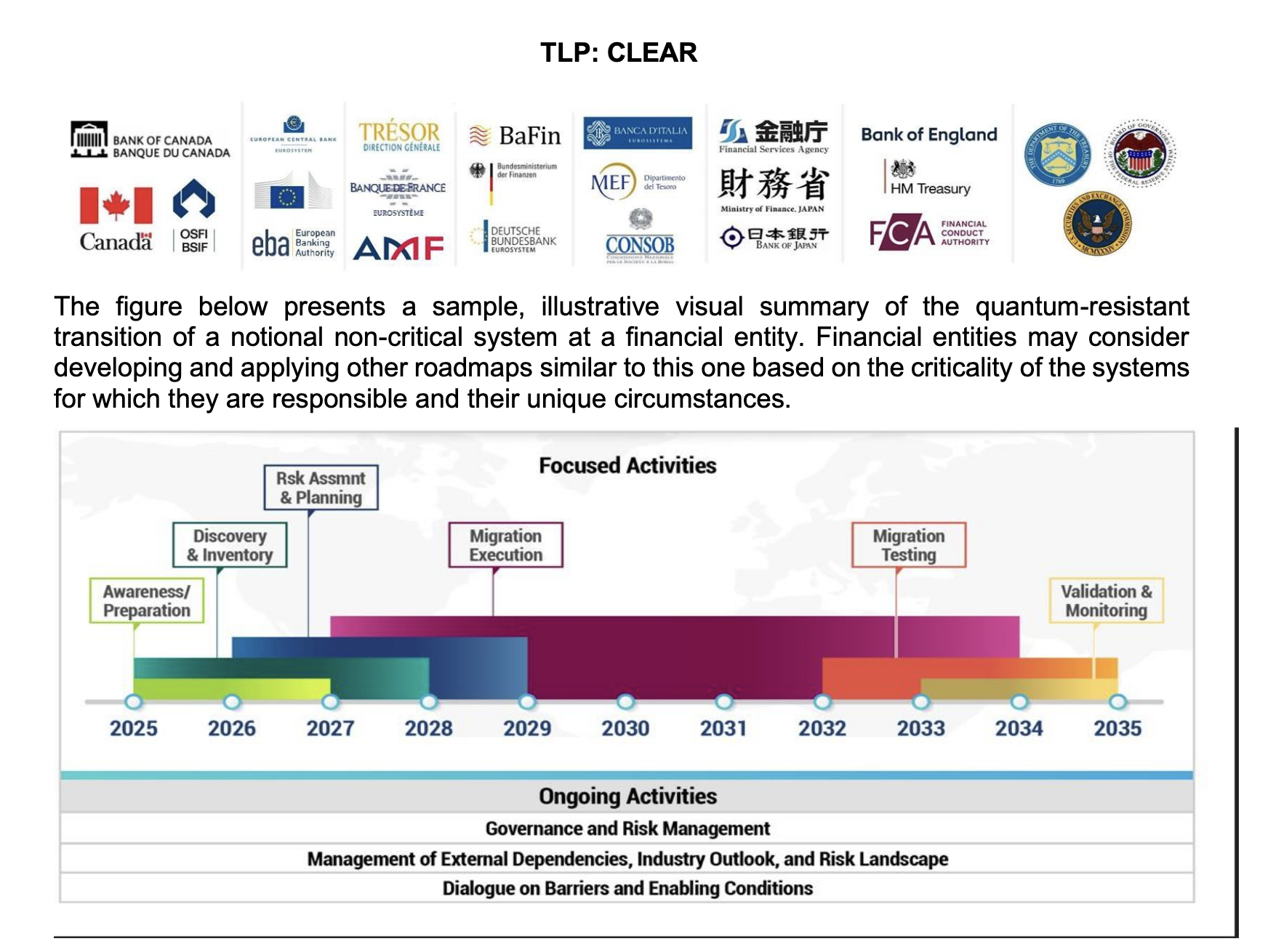
A Phased Model for Migration
The roadmap organizes migration activities into overlapping phases. These phases are not linear mandates but a shared reference model for planning and coordination.
1. Awareness and Strategic Readiness
Organizations establish executive-level understanding of quantum risk, assign accountability, define governance roles, and identify critical systems, sensitive data, and communication pathways.
2. Discovery and Inventory
Institutions develop comprehensive inventories of cryptographic assets, protocols, and vendor dependencies, while authorities assess ecosystem-wide maturity and capability gaps.
3. Risk Assessment and Planning
Tailored migration plans are developed for critical and non-critical functions, governance processes are adapted, and interoperability considerations are addressed to support sector-wide consistency.
4. Migration Execution
Quantum-resistant solutions are progressively deployed, beginning with priority systems. Migration pacing is adjusted as threat intelligence and technology maturity evolve.
5. Testing and Resilience Exercises
Migrated systems are validated through testing and scenario exercises, with quantum-resilience considerations increasingly embedded into supervisory reviews and crisis simulations.
6. Validation and Continuous Monitoring
Institutions incorporate new cryptographic standards, refine controls, and sustain improvement through ongoing oversight aligned with the evolving quantum threat landscape.
Continuous Activities That Span All Phases
Certain efforts are expected to run in parallel throughout the transition:
- Governance and Risk Management: Embedding quantum-safe requirements into existing institutional and supervisory frameworks.
- External Dependency Management: Tracking the maturity of standards, vendor solutions, and quantum capabilities.
- Structured Stakeholder Dialogue: Facilitating information sharing, issue identification, and collective problem-solving across the sector.
Timing the Transition: Why 2035 Matters
Predicting the arrival of cryptographically relevant quantum computers remains inherently uncertain. Nevertheless, comparable timelines are essential to ensure coordination and to avoid leaving critical data exposed under a “harvest now, decrypt later” threat model.
Based on inputs from governments, standards bodies, and industry experts, many jurisdictions reference 2035 as a reasonable outer target for broad post-quantum migration. This aligns with guidance from National Institute of Standards and Technology, international standard-setting organizations, and assessments of quantum technology development trajectories.
Importantly, the roadmap encourages earlier action for the most critical systems, with many institutions targeting the early 2030s for high-impact functions. These timelines are explicitly non-binding and should be adjusted as threats, standards, and operational realities change.
Moving from Planning to Collective Resilience
The G7 Cyber Expert Group emphasizes that many organizations have already begun implementing quantum-resistant techniques—such as hybrid cryptographic approaches—and that early adoption should be encouraged, not delayed. Equally important is designing systems for cryptographic agility, recognizing that future transitions will be inevitable as technology evolves.
The Group calls on financial authorities and institutions to integrate post-quantum considerations into governance, risk management, and technology strategies, maintain sustained executive engagement, and prioritize efforts based on systemic importance.
In parallel, the G7 Cyber Expert Group commits to continued cross-border coordination, engagement with standards bodies, dialogue with technology providers, and ongoing monitoring of quantum threats and migration lessons learned.
G7 Cyber Expert Group
Post-quantum cryptography is no longer a theoretical concern for financial services. It is a long-horizon operational challenge that demands early planning, coordinated execution, and shared accountability. The G7 roadmap provides a common language and strategic foundation—not a rulebook—for navigating one of the most significant cryptographic transitions the financial system has ever faced.