
With over 2000 fines instated and almost 5 billion euros fined total in the GDPR alone, PII is becoming increasingly important to secure. Businesses must implement a thorough PII compliance checklist to avoid regulatory penalties, sensitive consumer data loss, and reputational damage.
Let’s explore what PII compliance encompasses, how to implement a PII compliance checklist, and the best personal data protection practices businesses can implement to prevent PII loss.
Key Takeaways
- PII compliance includes procedures and frameworks used to safeguard PII.
- A PII compliance checklist covers the classification of PII, consent management, and data minimization.
- Your business’s PII compliance checklist should also include a PII policy, risk assessment and management strategy, and data security monitoring systems.
Cliff Notes for Compliance Checklist
Here’s a PII (Personally Identifiable Information) compliance checklist:
- Data Inventory and Classification: Conduct a comprehensive inventory of all PII within the organization. Classify the data based on sensitivity levels and establish clear policies for handling each category.
- Ensure all data sources are identified and documented.
- Classify data based on the level of sensitivity and regulatory requirements.
- Access Control and Security Measures: Implement strict access controls to ensure only authorized personnel can access PII. Use encryption, strong passwords, and multi-factor authentication to protect sensitive information.
- Regularly review and update access permissions.
- Use encryption for data at rest and in transit.
- Implement multi-factor authentication for systems handling PII.
- Policy and Training: Develop and enforce a comprehensive privacy policy. Provide regular training to employees on data protection practices, regulatory requirements, and the importance of safeguarding PII.
- Update privacy policies regularly to reflect current laws and best practices.
- Conduct regular training sessions and workshops for employees.
- Ensure employees understand their role in protecting PII and the consequences of non-compliance.
PII Explained
PII, or Personally Identifiable Information, covers any data that can be used to identify a unique individual. This could be anything from social security and names to a consumer’s date of birth and email address.
PII could include single data pieces or multiple data sets that can be combined to identify an individual. For example, you could use an individual’s name or genetic information to identify them without additional data, or you could use a combination of birthdate, address, and email.
Yes, the scope of PII is broad, which is why businesses need a solid PII compliance checklist to remain compliant with regulations that cover personal data.
What is PII Compliance?
PII compliance is a broad term that covers procedures and regulations that protect sensitive personal information. There’s no specific law that covers PII compliance. Instead, most major data privacy regulations cover PII in detail.
For example, the GDPR covers the collection, storage, and transfer of personal data, regardless of whether it’s collected through an automated or manual process.
Similarly, the VCDPA and CPRA are state-level laws that address personal data collection and enforce fines for non-compliance. However, the scope of these regulations is limited.
Other regulations that cover the protection of personally identifiable information include industry-specific regulations such as HIPAA, age-specific regulations such as COPPA, and data processing standards like the PCI DSS for payment processing.
In short, PII compliance defines the procedures for regulating PII data collection, storage, and usage. For businesses, setting a PII compliance framework and encrypting data could help with data privacy regulatory compliance and prevent a fallout caused by poor management of sensitive data.
PII Compliance Checklist
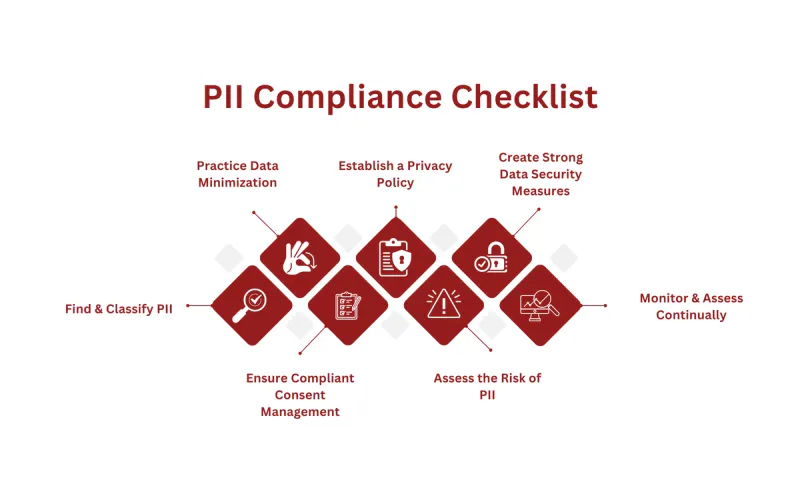
Since no single PII compliance regulation covers all industries and regions, you’ll have to implement procedures specific to your business’s needs. The best way to do so is through a data protection officer, but even they will adhere to specific compliance procedures.
Here are a few points to include in your PCI compliance checklist, regardless of the industry or region your business operates:
Find & Classify PII
Before you can implement a PII compliance policy, you’ll need to determine what type of sensitive personal information is collected, where it’s stored, and what it’s used for. Considering the scale of information many businesses handle nowadays, keeping an accurate and up-to-date record of PII can be challenging.
Remember that you’ll need to classify data according to industry standards when classifying PII. What may constitute private data for businesses falling under the CPRA may not necessarily be PII under the GDPR or HIPAA.
Businesses can also classify data according to level of importance and how frequently it’s used. You can encrypt rarely accessed PII and limit access logs to reduce the risk of data leaks.
Finding and classifying data includes:
- Implementing a continuous data mapping system.
- Doing regular data audits to ensure PII is properly classified.
- Finding gaps in the data classification process – you can do this by converting all data to a single format, eliminating duplicate and lost data.
- Gaining access to stored data and data currently in use and limiting access points.
- Assigning a sensitivity level to classified data.
Practice Data Minimization
If your business collects PII, a good way to reduce the risk of data loss is to practice data minimization. When your business only collects PII that’s necessary, it becomes much easier to keep track of where the data is stored and for what purpose it’s used.
Data minimization is also a key part of data privacy regulations. Article 5(1)(c) of the GDPR states that data collection should be “limited to what is necessary”.
Data minimization also reduces the burden of storing large volumes of historical data and categorizing irrelevant data.
While the concept is simple, you’ll need to implement certain principles of data minimization, including:
- Follow a limited data collection approach and link each data collection task to a specific purpose.
- Practice anonymization where possible. This may include replacing consumer names with unique numbering or using pseudonyms to minimize personal data storage.
- Ensure accuracy and transparency in data collection and storage.
- Retain data only for as long as needed. You could do routine data audits to determine which data sets are irrelevant and delete them accordingly.
Ensure Compliant Consent Management
Minimizing data collection can help reduce data loss risks, but your business can still face penalties if you collect personal data without having proper consent. Compliant consent management covers consent collection, processing, storage, and implementation.
Most major data privacy laws require businesses to get explicit consent when collecting consumers’ personally identifiable information. They cover a wide range of consent types, including cookie consent, general consent, and explicit consent.
To implement compliant consent management, a business should communicate:
- How it collects consumers’ personal data
- What data it need consent for?
- Why it needs the data
- Which third parties the data will be shared with, if any?
When using third-party platforms or software for consent management, you’ll need to review their policies and ensure they’re compliant with data regulations.
Establish a Privacy Policy
The next and most important step of your PII compliance checklist is to create a privacy policy governing data usage, audits, data governance, and risk mitigation. Your internal privacy policy will closely correlate with industry and other regulatory requirements.
A typical privacy policy will cover basic aspects of PII, including:
- Data collection: Ensure the collection process is legal, fair and collected with prior consent.
- Data usage: Your business’s data usage policy should cover who can access data, how log access is restricted and monitored, and where PII can be used.
- Data governance training: There’s no point in creating a PII policy without communicating it to employees. Set scheduled training and development sessions to reduce the risk of human error when implementing your PII policy.
- Data mapping: Your PII policy should also include an auditing and data mapping process so the business can rectify gaps in the policy implementation
- Data breach procedures: With over 59% of businesses affected by breaches caused by third parties, there’s always a possibility of your business being affected. As a business, it’s important to have procedures in place to notify individuals when breaches occur so they can protect their data.
Assess the Risk of PII
While there’s no foolproof system for eliminating PII risk, you can always minimize it with regular data protection impact assessments. PII DPIAs may include regular compliance and data security audits to identify gaps in your PII policy implementation.
Considering the pace at which data compliance regulations change, you may want to implement more regular data audits.
And since not all businesses can afford a full-time compliance officer for auditing, it’s best to outsource compliance to a third-party specialist like Captain Compliance. Our compliance specialists can assess PII risks more accurately and ensure your business achieves corporate compliance.
Create Strong Data Security Measures
While you can’t eliminate PII risk, you can reduce it with data security measures. This covers procedures to encrypt and protect data against hackers, malware, or human negligence.
Basic data security measures include:
- Establish strong access control measures.
- Ensure strong network security measures (firewalls)
- Using end-to-end data encryption.
- Implementing anti-malware software.
- Use strong passwords and multifactor authentication.
- Train employees on data security measures.
- Delete unnecessary PII that is no longer needed.
Remember, the weakest data link in any business is usually employees, so it’s important to conduct regular training sessions on cybersecurity procedures for employees.
Monitor & Assess Continually
The final step to ensuring PII compliance is having a continuous monitoring system to ensure your business remains compliant with data regulations. Continuous monitoring of your business’s data systems also helps identify breaches promptly.
Security standards like the ISO 27000 or PCI DSS may also require a continuous monitoring strategy for protecting sensitive data.
But continuous monitoring isn’t limited to regular audits (although it’s an important part of the process). Rather, it’s about implementing processes, tools, and frameworks to assess data risks in real-time and having a contingency plan in place when breaches do occur.
To implement continuous monitoring in your business, you’ll need to:
- Create regular compliance audit schedules.
- Use tools that cover the businesses’ entire data system.
- Conduct regular privacy impact assessments.
- Create a clear action protocol for data loss prevention.
- Integrate risk management frameworks with your PII compliance policy.
FAQs
Are There Any Specific Regulations That Cover PII Compliance?
Most regulations will have some standard for protecting PII. This includes standards for the collection, storage, transfer, and usage of personally identifiable information.
Not sure which data protection laws govern PII? Read more here.
What is the Difference Between PII and SPI?
PII is a broad category that includes any information used to identify an individual, while SPI is a type of PII that includes sensitive information that could be used to harm an individual if leaked.
Read more about the difference between PII and SPI here.
What is the Best Way to Protect PII in a Business?
There’s no one specific strategy for protecting PII in a business. Instead, PII compliance includes a wide range of activities, from setting a PII policy to conducting DPIAs and more.
Not sure what a DPIA should include? Read more about DPIAs here.
What Should My Business Do if PII is Leaked?
Like with other data breaches, businesses need to have a contingency plan in place in case of a PII data breach. This includes stopping data collection/processing, informing consumers, and setting more stringent protocols to prevent future leaks.
Hit by a data breach recently? Let Captain Compliance strengthen your data compliance systems!
How Can Captain Compliance Help?
The biggest challenges of PII compliance are conducting regular audits and implementing a checklist that ensures thorough compliance. At Captain Compliance, we help businesses safeguard PII through regular audits, data management frameworks, and other compliance services.
Get in touch today for a complimentary consultation, and we’ll ensure your business’s PII compliance is in accordance with industry and data security regulations.